Aws Cloudhsm Vs Kms
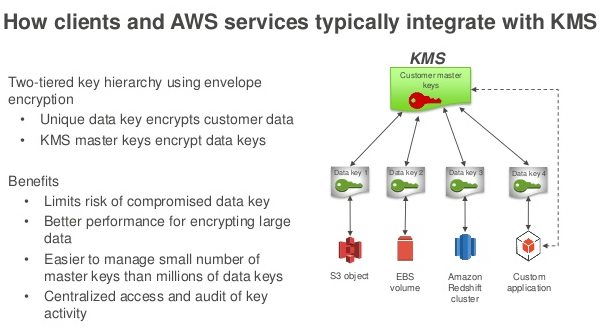
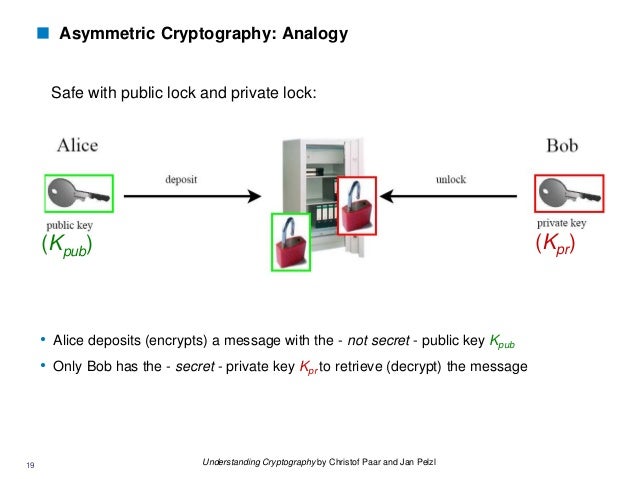
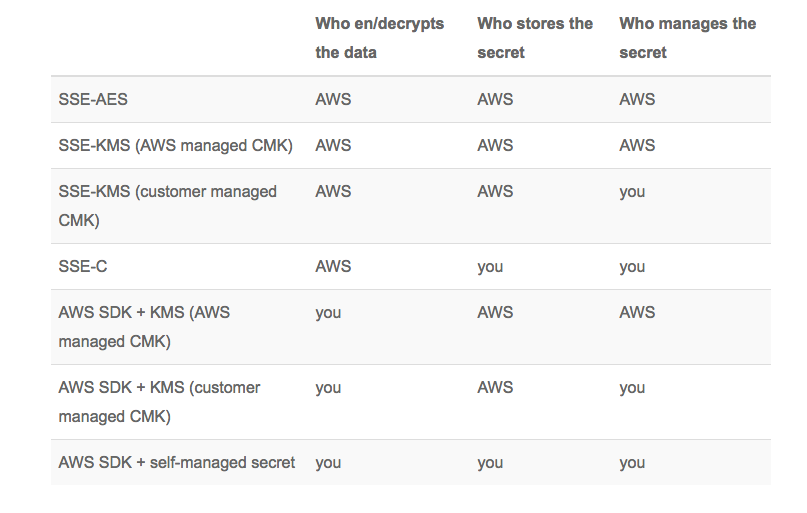
The ownership and responsibility for management, storage, and tracking of the data keys lie solely with the application owner.

Aws cloudhsm vs kms. Elastic Container Service (ECS) Fargate Container Instances:. AWS WAF LDAP and AD on AWS 10 - CLOUDTRAIL. But you can with CloudHSM.
Cloud KMS allows you to create, use, rotate, automatically rotate, and destroy AES256 symmetric and RSA 48, RSA 3072, RSA 4096, EC P256, and EC P384 asymmetric cryptographic keys. If you want to use the server-side encryption offered by many AWS services (such as EBS, S3, or Amazon RDS), you can do so by configuring a custom key store in AWS KMS. What are the AWS KMS?.
Azure Container Instances is the fastest and simplest way to run a container in Azure, without having to provision any virtual machines or adopt a higher-level orchestration service. There is yet a simpler version of HSM in AWS which can be used as an HSM, and it is called AWS KMS. AWS KMS vs CloudHSM?.
Amazon Web Services Key Management Services (AWS KMS):. A service providing you with secure cryptographic key storage by making Hardware Security Modules (HSMs) available on the AWS cloud. Features Usage & Limitations 11 - STORAGE GATEWAY.
9 - SECURITY ON AWS. The answer to this question is different depending on whether you deploy AWS KMS, CloudHSM, or a third-party encryption key manager like Townsend Security’s Alliance Key Manager. AWS service Azure service Description;.
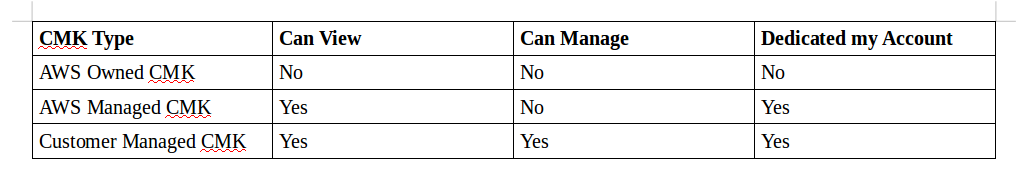
If someone compared CloudHSM vs KMS offered by AWS, the primary advantage is that CloudHSM is available to any enterprise, and not just AWS users. In AWS, it’s call AWS HSM while in Azure, it’s call KeyVault. Data Keys are generated, encrypted and decrypted by CMKs.
In this course, Securing Data on AWS, you will gain the ability to encrypt your data using any of the data services provided by Amazon Web Services (AWS). Organizations use these features to satisfy compliance demand for data security. When you use the AWS CloudHSM service you create a CloudHSM Cluster.
The two types of encryption keys in AWS KMS are Customer Master Keys (CMKs) and Data keys. AWS has announced new custom key stores backed by CloudHSM. AWS CloudHSM helps you comply with strict key management requirements without sacrificing application performance.
KMS supports custom key stores backed by AWS CloudHSM clusters. This is an essential matter that must be answered before using the AWS cloud system. Also it covers the differences between AWS Key Management Service and AWS CloudHSM.
Comparison of AWS CloudHSM vs. You can highlight the text above to change formatting and highlight code. AWS KMS is a managed service that is used to create and manage encryption keys.
You can configure your own CloudHSM cluster and authorize KMS to use it as a dedicated key store for your keys rather than the default KMS key store. You also need to create a dedicated crypto user (CU) in the cluster's HSMs that AWS KMS can use to create and manage keys on your behalf. When to use KMS.
AWS CloudHSM rates 4.3/5 stars with 12 reviews. In which scenario would you prefer CloudHSM over AWS KMS?. Amazon Web Services Navigating GDPR Compliance on AWS 5 In addition, the flexibility and control that the AWS platform provides enables customers to deploy solutions that meet several industry-specific standards 3.
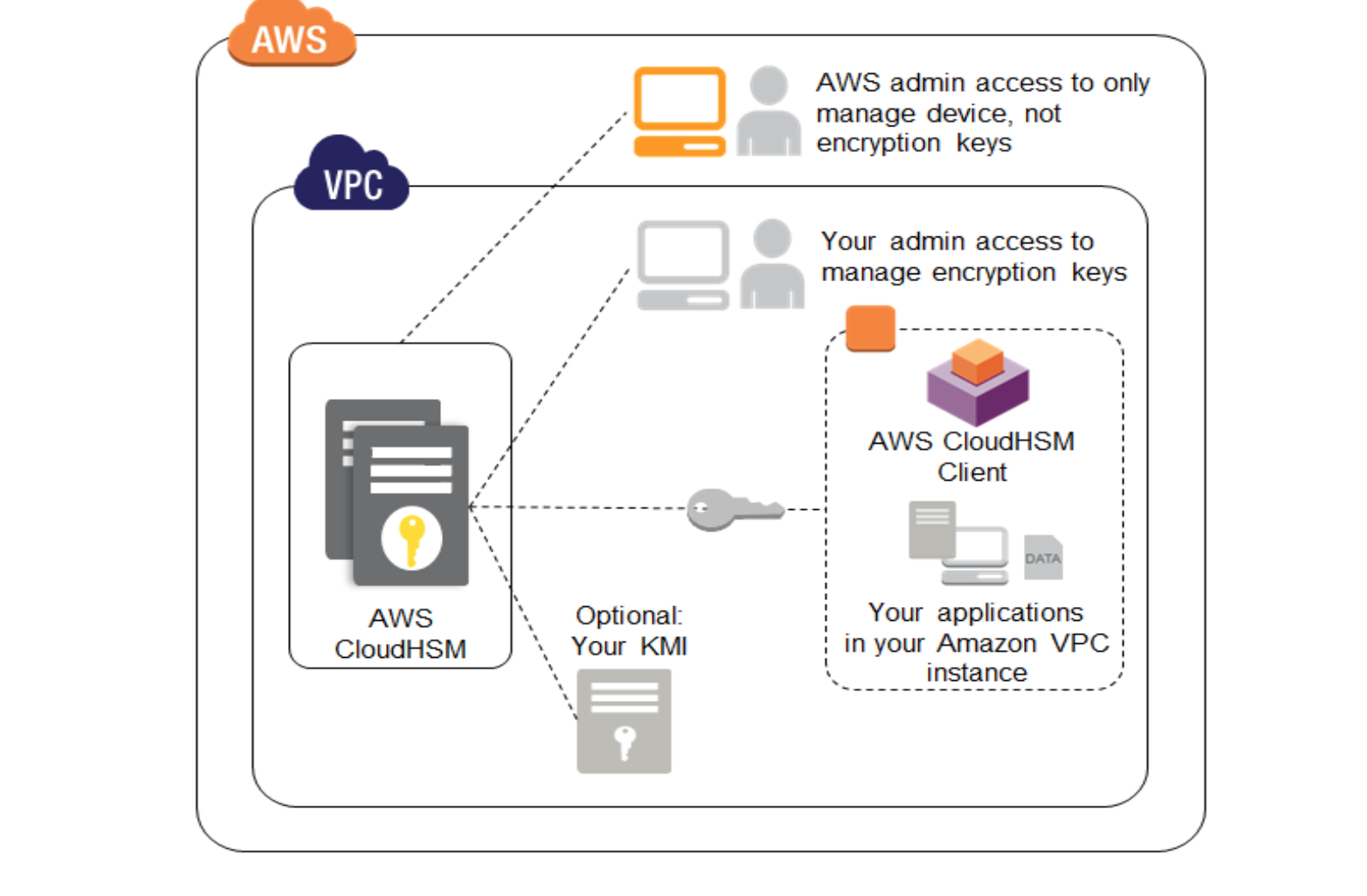
It should be appealing to startups or small. The AWS CloudHSM service provides single-tenant access to each HSM within an Amazon Virtual Private Cloud (VPC). The AWS Certified SysOps Administrator Associate ( SOA-C01 ) exam is specifically designed to validate the technical knowledge of AWS SysOps Administrators, Systems Administrators, and those in a DevOps role who create automatable and repeatable deployment of applications, networks, and systems on the AWS platform.
KMS THINGS CAN GET CONFUSING FOR END-USERS when the same acronym can be used to describe two completely different types of key managers. AWS services integrate with AWS Key Management Service, which in turn is integrated with AWS CloudHSM through the KMS custom key store feature. The AWS Certified Solutions Architect - Associate video course is a vital tool to prepare for your SAA-C02 upcoming certification assessment.
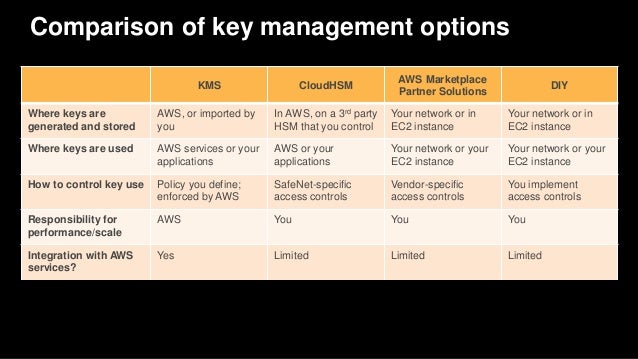
The second option, AWS KMS, is an ideal solution for organizations that want to manage encryption keys in conjunction with other AWS services. You can connect directly to AWS KMS through a private endpoint in your VPC instead of connecting over the internet. A key store is a secure location for storing cryptographic keys.
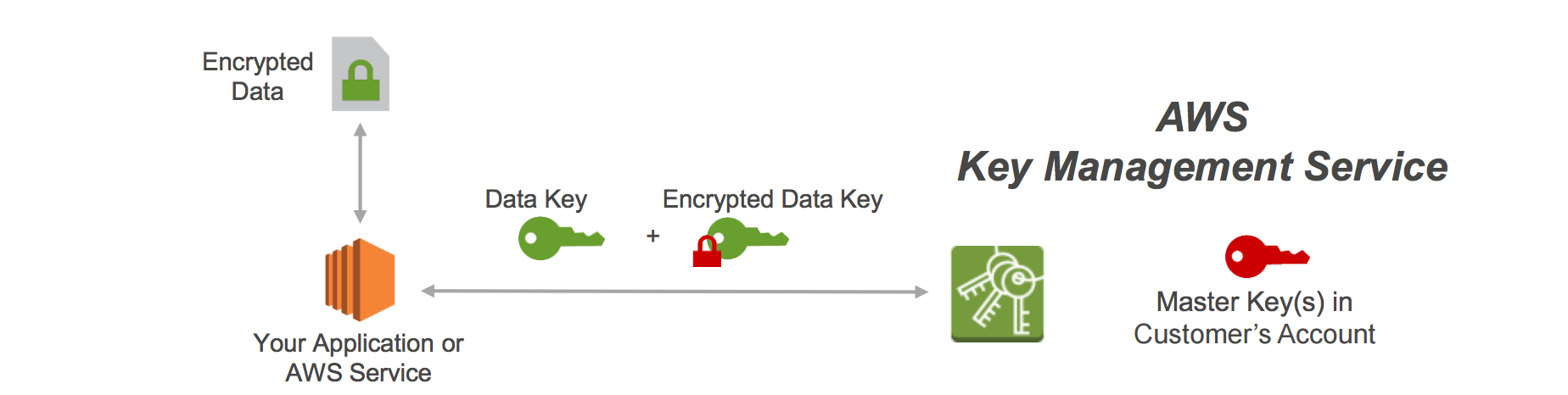
This plaintext data key is used to encrypt the data, then the plaintext key is removed ASAP from the memory so that data doesn’t get compromised. HSM instances in a cluster are automatically synchronized and load-balanced. Here’s some background and a summary of what this means.
AWS KMS is used to generate, encrypt, and decrypt data keys but does not manage, store, or track their usage. Each product's score is calculated by real-time data from. The AWS KMS custom key store feature combines the controls provided by AWS CloudHSM with the integration and ease of use of AWS KMS.
These solutions are either a physical hardware. Sections of this page. In comparing to AWS HSM, AWS KMS is.
That is because CloudHSM can encrypt, store, and decrypt data to and from any cloud services around the globe. You can use the keys to encrypt up to 64kB, so again this. How to use KMS.
The keys always stay inside AWS so you can't lose them or have someone steal them. AWS CloudHSM AWS CloudHSM is a dedicated, tamper-proof, hardware appliance solution to provide. However, AWS CloudHSM provides a dedicated, FIPS 140-2 Level 3 HSM under your exclusive control, directly in your Amazon Virtual Private Cloud (VPC).
AWS Key Management Service (KMS) rates 4.3/5 stars with 27 reviews. Với AWS CloudHSM, cung cấp dịch vụ mà encrypt-key chỉ duy nhất bạn có quyền truy cập. The grouping of these tiered hosts forms the AWS KMS stack.
Clusters can contain multiple HSM instances, spread across multiple Availability Zones in a region. However, you might want to stick with AWS KMS if you're looking for a completely managed encryption experience. Used for temporary, granular permission.
AWS CloudHSM provides a dedicated, FIPS 140-2 Level 3 HSM under your exclusive control, directly in your Amazon Virtual Private Cloud (VPC).". On the other hand, AWS Key Management Service is detailed as " Easily create and control the encryption keys used to encrypt your data ". You should use Key Policies for static permissions and for explicit deny.
First, you will learn the difference between the Key Management Service (KMS) and CloudHSM. CloudHSM allows full control of your keys such including Symmetric (AES), Asymmetric (RSA), Sha-256, SHA 512, Hash Based, Digital Signatures (RSA). Another new announcement was made by AWS here at re:Invent, this time in the popular security category.
Although enabling encryption looks quite trivial, managing the underlying Key management lifecycle processes and handling the associated cryptographic operations. "AWS Key Management Service (KMS) is a multi-tenant, managed service that allows you to use and manage encryption keys. Ideally, Cloud HSM refers to appliances hosted in physical data centers, which are surveillance proof against PCI DSS AND SOC framework.
If you are given a choice between 2, which one would you prefer in your architecture?. A cloud service provider’s Key Management Service, such as AWS KMS, is a multi-tenant, encryption key storage service managed by AWS that provides a subset of encryption key lifecycle management. HSMs in Amazon’s data centers.
Compare AWS CloudHSM vs AWS Key Management Service (KMS) Save See this. AWS - Certified Security Specialty (Infrastructure Security (AWS KMS (Key…:. AWS provides a wide range of information regarding its IT control environment to.
For the purposes of this question, we can put AWS’s Cloud HSM and third-party key managers in the same category. All requests to AWS KMS must be made over the Transport Layer Security protocol (TLS) and terminate on an AWS KMS host. Should we choose AWS CloudHSM instead of AWS KMS.
AWS Key Management Service (KMS) is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data, and uses Hardware Security Modules (HSMs) to protect the security of your keys. How does AWS KMS compare to AWS CloudHSM?. Who this course is for:.
AWS KMSとCloud HSMの違い AWS CloudHSM AWS Key Management Service 専有性 VPCにお客様専用のハードウェアデバイス(Safe Net Luna SA 7000 HSM)をインストール。. What is AWS Key Management Service?. We’ll write more about that in a future article.
Note that we are now logged into both HSM nodes in the cluster. The Key Management Service (KMS) stores and generates encryption keys that can be used by other AWS services and applications to encrypt your data. Another CloudHSM benefit is only you -- not AWS -- have access and control of the keys you create.
What services support KMS. KMS is a key management service. With CloudHSM, you pay an hourly fee for each HSM you run.
December 13, 19 at 11:30 PM · ·. When you create keys in KMS you can chose to generate the key. On Encryption and Key Management in AWS – Comparing KMS vs.
AWS KMS hosts only allow TLS with a ciphersuite that provides perfect forward. However, there are AWS CloudHSM quotas, such as a quota on the number of AWS CloudHSM clusters in each AWS account and Region, and AWS KMS quotas on the use of CMKs in a custom key store. In particular, it offers an outline as well as detailed lectures on all the objectives of SAA-C02.
Anyone learning and using AWS. We log in as the CO admin user to create our new kmsuser CU account. Each AWS KMS custom key store is backed by an AWS CloudHSM cluster.
What are the Hardware Security Modules CloudHSM ?. AWS Key Management Service (AWS KMS) AWS KMS is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data. Configuration Options & Architecture Gateway Cached Vs Gateway Stored Pricing Use Cases.
How does AWS CloudHSM vs KMS compare?. In contrast to AWS CloudHSM, AWS KMS provides a complete set of tools to manage encryption keys, develop applications and integrate with other AWS services. Topics included in this course:.
AWS - Certified Security Specialty. Và nó cũng tương tự với bất cứ dịch vụ cloud nào chứ không chỉ riêng AWS. A crypto user (CU) is a CloudHSM user that has permissions to perform key management and cryptographic operations.
AWS KMS is a tiered service consisting of web-facing KMS hosts and a tier of HSMs. 7 1 Asked 2 years ago. AWS Key Management Service (KMS) based on data from user reviews.
Cloud HSM gives you your own hardware module, within a single-tenant storage. Press alt + / to open this menu. With HSM, encrypt, decrypt, and sign with AES-256 symmetric and RSA 48, RSA 3072, RSA 4096, EC P256, and EC P384 asymmetric cryptographic keys.
Like KMS, the CloudHSM system uses stand-alone hardware appliances to store cryptographic keys, but it costs $5,000 up front plus hourly charges. Both services offer a high level of security for your cryptographic keys. You have exclusive control over how your keys are used via an authentication mechanism independent from AWS.
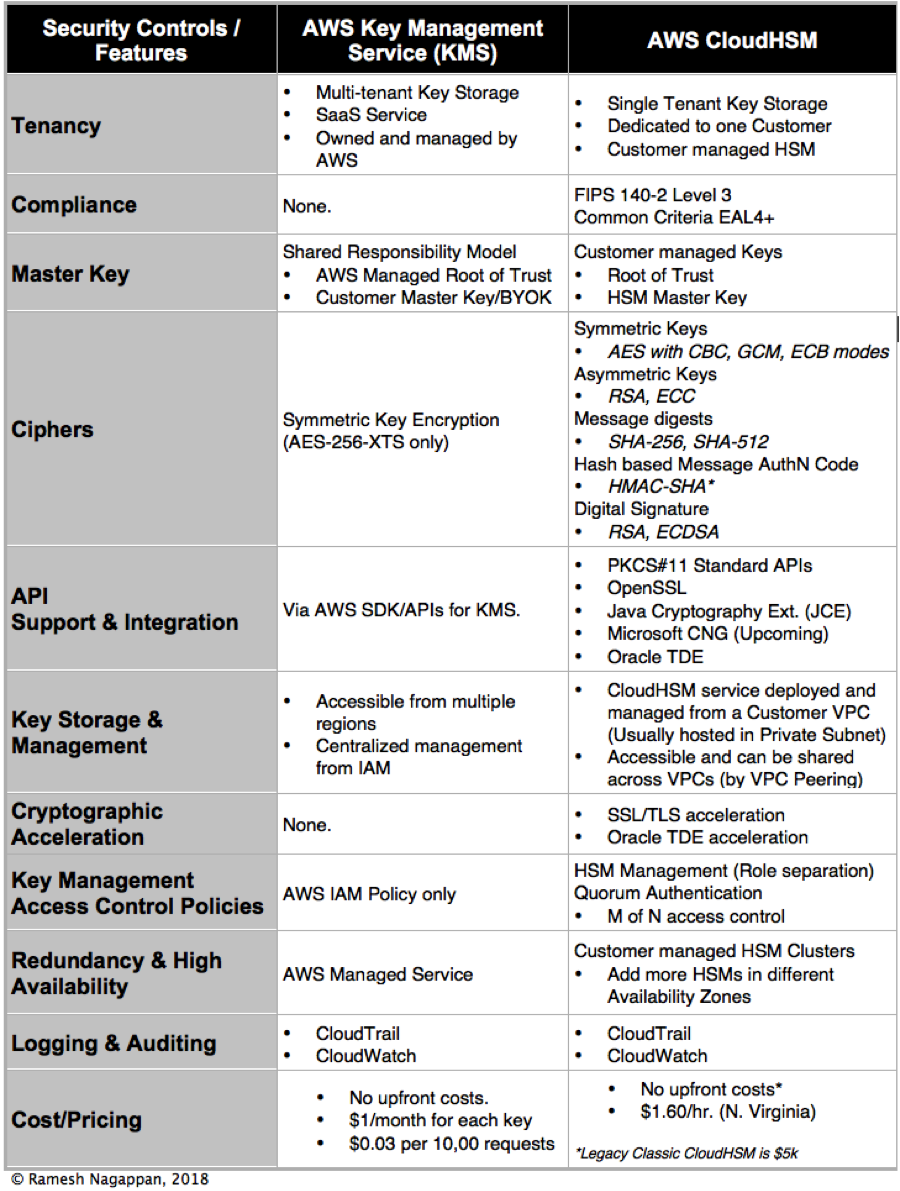
AWS CloudHSM provides single tenant key storage giving FIPS 140-2 Level 3 compliance. The table below describes the latest version of CloudHSM and how it differs from its predecessor:. Build Cloud Solution Architects.
To create a custom key store, you must specify an active AWS CloudHSM cluster that is not already associated with another key store. AWS CloudHSM is a security service that offers isolated hardware security module (HSM) appliances to give customers an extra level of protection for data with strict corporate, contractual and regulatory compliance requirements. Note If the KMS doesn’t give you the cryptographic functionality you need, Amazon also have a Cloud-hosted HSM available which offers a PKCS#11 interface.
CMKs can be used to encrypt and decrypt up to 4-kilobytes of data. It can eliminate the cost and overhead of provisioning HSMs in your data center as your data and processing demands grow. Với AWS KMS, cung cấp dịch vụ mà encrypt-key được truy cập bởi cả bạn và Amazon.
AWS KMS AWS CloudHSM AWS Certificate Manager (CloudFront ELB certificates) DDOS protection:. KMS is shared hardware tenancy - you keys are in their own partition of an encryption module shared with other AWS customers, each with their own isolated partition. The crypto details are here (not stick figures :-( ) According to the book it's only for symmetric key management (generation, store, enable/disable, delete).
AWS KMS then uses the specified CMK to generate data keys. Regions AWS KMS supports custom key stores in all AWS Regions where both AWS KMS and AWS CloudHSM are available. AWS KMS lets you create keys that can.
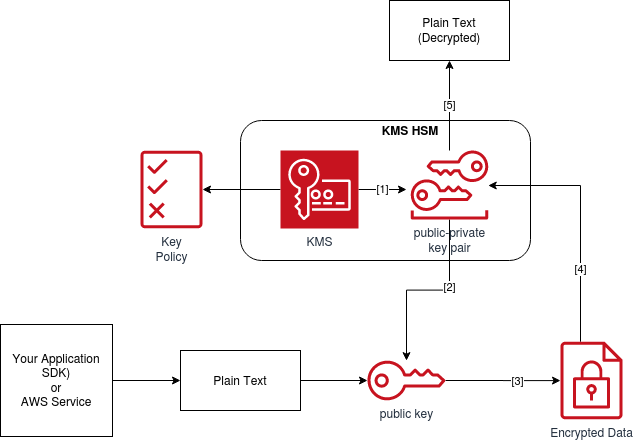
So back to the plot, what does AWS KMS and AWS CloudHSM do?. As you can see from the below figure it generates one plaintext data key and an encrypted data key. A secure data protection using encryption depends more on secure key management processes than the encryption itself.
When solely comparing AWS KMS vs Cloud HSM one can look at the following factors:. AWS Key Management Service (KMS) AWS Key Management Service (KMS) is a multi-tenant, managed service that allows you to use and manage encryption keys. AWS CloudHSM provides you with a FIPS 140-2 Level 3 overall validated single-tenant HSM cluster in your Amazon Virtual Private Cloud (VPC) to store and use your keys.
What are AWS Cloud Hardware Security Modules CloudHSM?. AWS KMS will use the kmsuser account to administer our custom key store.

Hsm Noise

How Secure Is Amazon S Key Management Service Aws Kms Interconnections The Equinix Blog
The Fundamental Security Concepts In Aws Part 2 Dzone Security
Aws Cloudhsm Vs Kms のギャラリー

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
Kms Jayendra S Blog

Amazon Cloud Hardware Security Module Hsm Cloudhsm Exam Tips

Aws Re Inforce 19 Achieving Security Goals With Aws Cloudhsm Sdd333 Youtube

Aws Cloudhsm Digital Cloud Training
Aws Encrypting Data At Rest Whitepaper Certification Jayendra S Blog
D1 Awsstatic Com Events Reinvent 19 Repeat 1 Achieving Security Goals With Aws Cloudhsm Sec305 R1 Pdf

Amazon Cognito Vs Aws Key Management Service What Are The Differences

Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium
The Fundamental Security Concepts In Aws Part 2 Dzone Security

Aws Re Invent 16 Get The Most From Aws Kms Architecting Applicati

A Comparison Of Secrets Managers For Aws Scalesec

New Custom Key Stores In Kms Backed By Cloudhsm Cloud Academy
D1 Awsstatic Com Whitepapers Aws Securing Data At Rest With Encryption Pdf

Cloud Security Specialty 2 Flashcards Quizlet

Protecting Your Data With Aws Kms And Aws Cloudhsm

Aws Kms Noise

Aws Kms Vs Aws Cloudhsm

Are Kms Custom Key Stores Right For You Aws Security Blog

Aws Developer Prep Data Science Portfolio

Aws Key Management Service Aws Kms Tutorials Dojo

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Hsm Aws Security Blog

Aws Cloudhsm Vs Aws Key Management Service What Are The Differences
S3 Storage Encryption With Aws Cross Account Kms Key Filecloud Filecloud Support
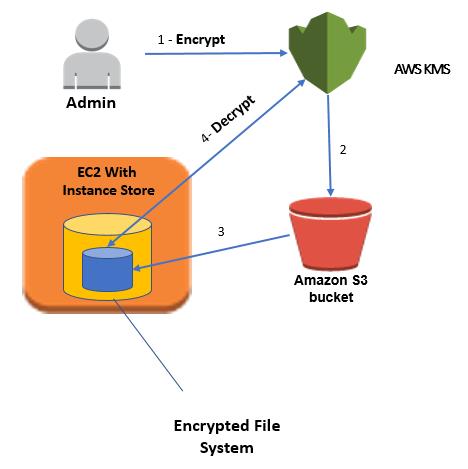
What Is Aws Kms Tutorial Links

Aws Cloudhsm Digital Cloud Training
What Is The Aws Equivalent Of The Azure Key Vault Quora

Protecting Your Data With Aws Kms And Aws Cloudhsm

Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium
Cloud Crypto Providers Aws Vs Google Vs Azure Cryptosense

Gcp Kms Fips
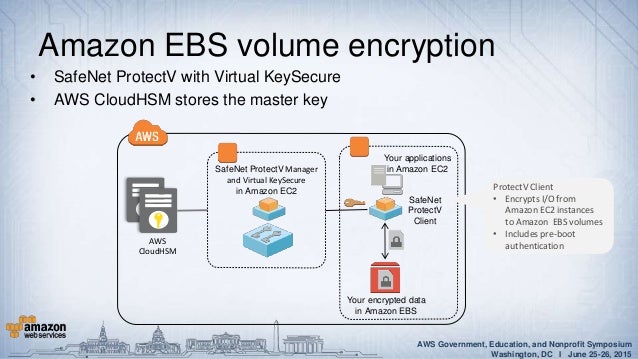
Protecting Your Data With Aws Kms And Aws Cloudhsm

Are Kms Custom Key Stores Right For You Aws Security Blog

Cloud Hsm Archives Cryptosense
Q Tbn 3aand9gcq7 Cbw5ng7lvptj5q1pancuyy1uywzmthq9w0jldsg1pi6qvtm Usqp Cau
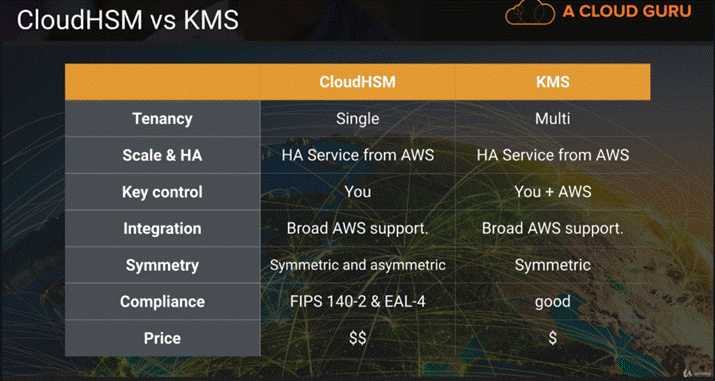
Kms
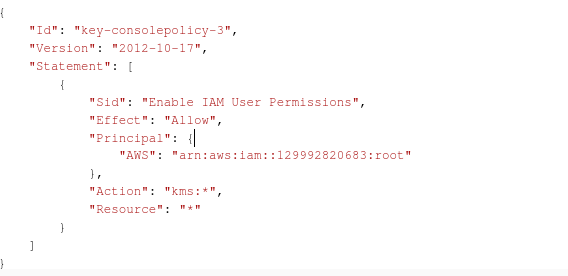
Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog
Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium
The Hitchhiker S Guide To The Cloud Aws Vs Gcp Vs Azure And Their Ai Ml Api S Capabilities

How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm Aws Security Blog

Amazon Web Services Security Overview Webstep No
Chapter 11 Aws Kms And Aws Cloudhsm
Aws Re Invent 16 Get The Most From Aws Kms Architecting Applicati
Q Tbn 3aand9gctjoqbprigsfyidks Aqr1uehsxbdgw8gdecw5jx2q8dlot6ef7 Usqp Cau

Encryption And Key Management In Aws Youtube

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
Best Encryption Key Management Software In G2

Aws Cloudhsm
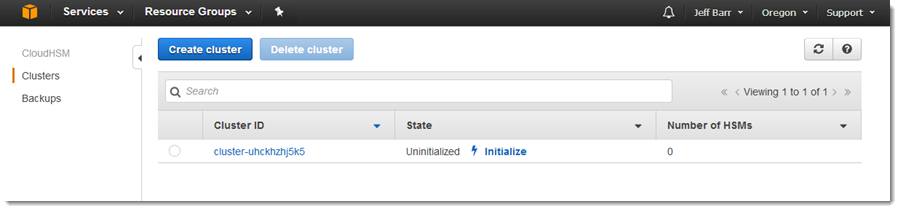
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog
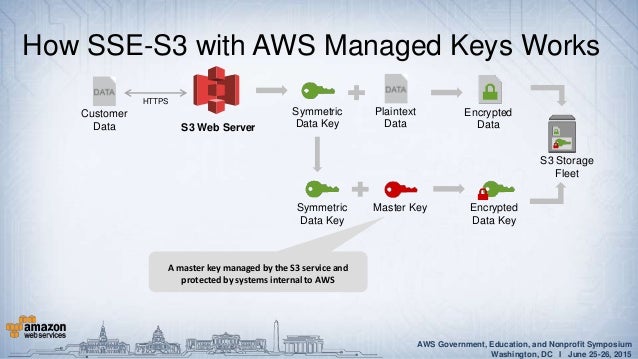
Protecting Your Data With Aws Kms And Aws Cloudhsm

How To Lower Costs By Automatically Deleting And Recreating Hsms Aws Security Blog

Key Management Service Noise
Cloud Netapp Com Hubfs Encryption white paper Netapp ultimate aws encryption guide Pdf T

Protecting Your Data With Aws Kms And Aws Cloudhsm

A Comparison Of Secrets Managers For Aws Scalesec

Using Aws Kms To Manage Secrets In Your Infrastructure

What Is Aws Hsm Aws Cloudhsm Tutorial Links
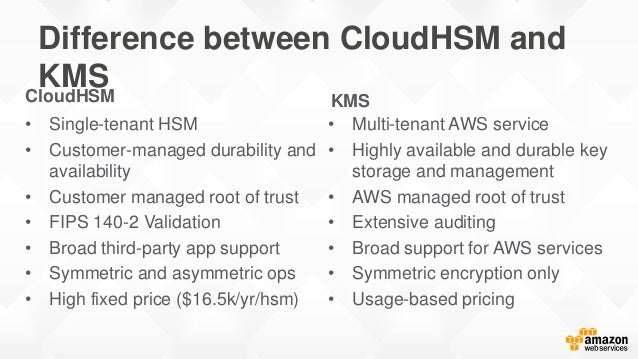
Deep Dive Aws Cloudhsm Classic
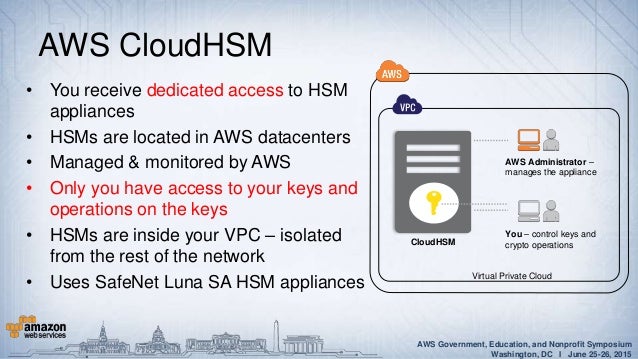
Protecting Your Data With Aws Kms And Aws Cloudhsm

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Aws Cloudhsm Vs Vault What Are The Differences

Pci Dss Are Aws Kms And Cloudhsm Suitable

Aws Cloudhsm Vs Aws Key Management Service What Are The Differences

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Aws Cloudhsm Reviews Details Pricing Features G2
Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium

Protecting Your Data With Aws Kms And Aws Cloudhsm

Architecting Security Governance Across Your Aws Accounts Part 3 Data Security On Aws By Ammar Alim Itnext
Q Tbn 3aand9gcrejirfjqubbxazmdeqo3z0prq3tjwvzfwo Nvp0ntb1sbxx7ln Usqp Cau

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Hipaa Compliance With Aws Pragtech Blogger

Protecting Your Data With Aws Kms And Aws Cloudhsm

Working With Customer Master Keys Cmks Using The Aws Kms Api Tutorials Dojo

Protecting Your Data With Aws Kms And Aws Cloudhsm

Aws Cloudhsm Cloud Data Architect
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog

Seguridad De La Informacion Redes Por David Romero Trejo

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Terabitweb Blog
Encryption And Key Management In Aws Comparing Kms Vs Cloudhsm Web Security Patterns

Overview Of Aws Kms And Aws Cloudhsm Encryption Consulting
Encrypting Sensitive Data Stored On S3 Dzone Security

How Secure Is Amazon S Key Management Service Aws Kms Interconnections The Equinix Blog

Aws Cloudhsm Aws Security Blog
What You Need To Know About Bring Your Own Key In The Cloud Techbeacon

Security Iteanz Com

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
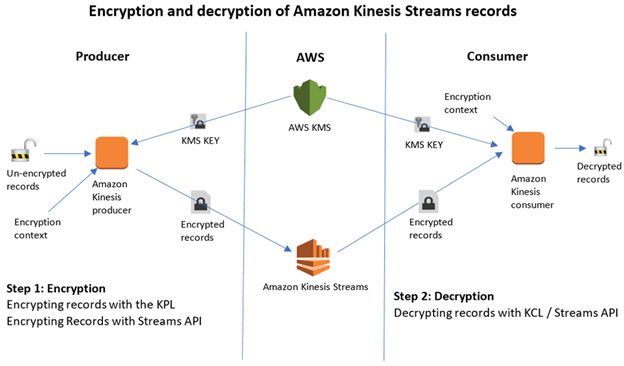
Aws Kms Testprep Training Tutorials

Aws Cloudhsm Digital Cloud Training

Aws Cloudhsm Noise
Hashicorp Aws Integrating Cloudhsm Vault Enterprise
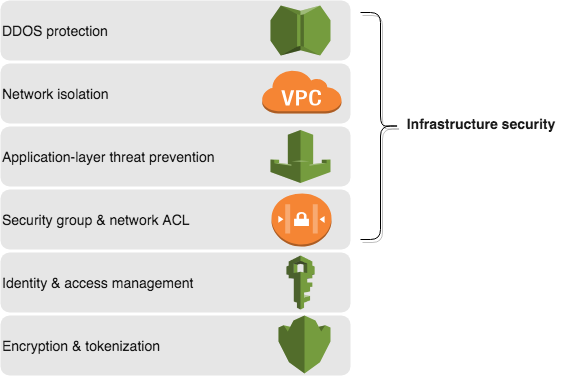
Determine Encryption Requirements Or Implementation Technologies Testprep Training Tutorials
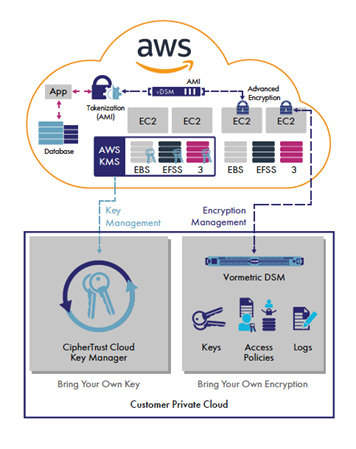
Advanced Encryption Solutions For Amazon Web Services Thales

Aws Kms Vs Cloudhsm Course Aws Certified Solutions Architect Professional 18
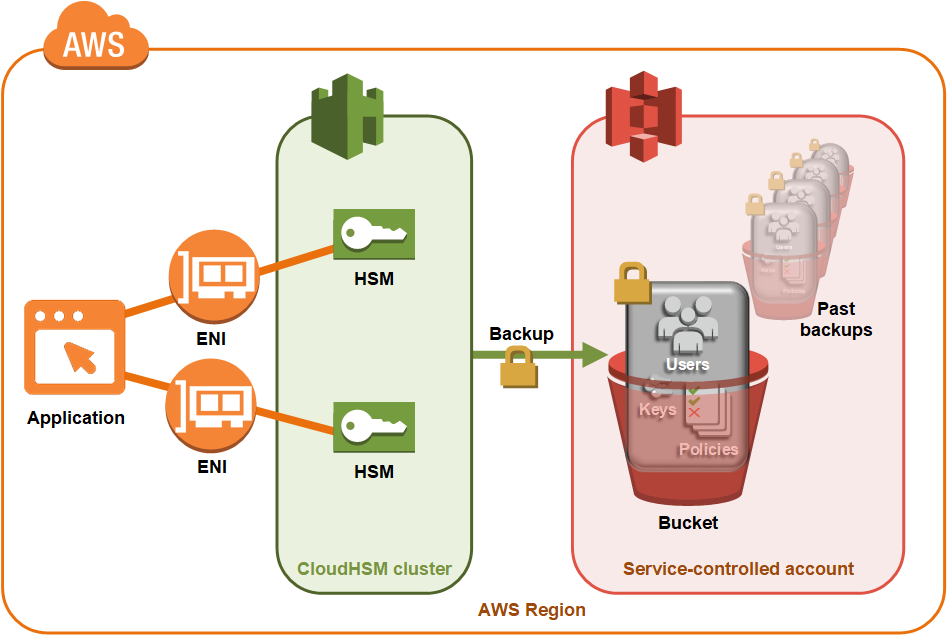
Aws Cloudhsm Cluster Backups Aws Cloudhsm
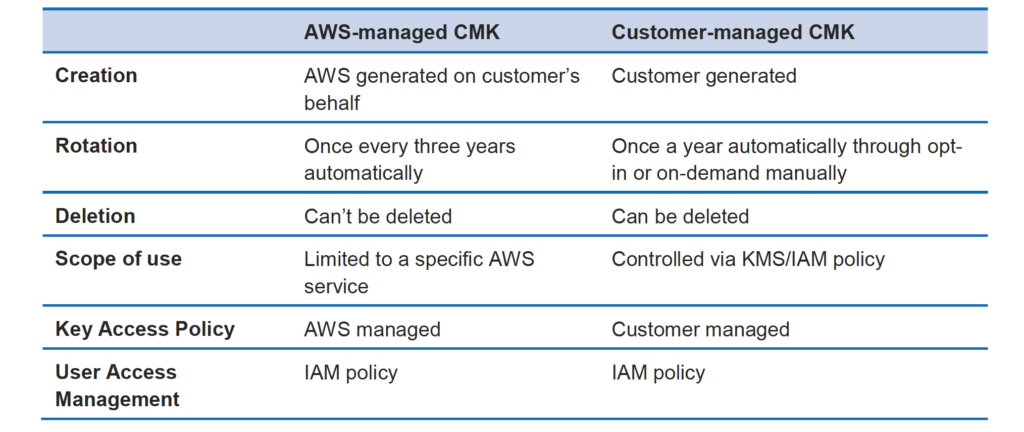
Kms Jayendra S Blog

Architecting Security Governance Across Your Aws Accounts Part 3 Data Security On Aws By Ammar Alim Itnext

How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm Aws Security Blog
Q Tbn 3aand9gcttkokbi5areayuoxmrq1rfruaqt8 Cos5up72wdkygedevwhz Usqp Cau

Aws Kms And Aws Cloudhsm Free Training Notes For The Aws Sysops Administrator Awscertifications



