Aws Cloudhsm Architecture
AWS Solutions Architect Associate exam overview.

Aws cloudhsm architecture. Business Case development, application assessment and migration planning, Cloud Operating Model design;. AWS owns the responsibility of provisioning the HSM in the customer's VPC environment in AWS. AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud.
Who is an AWS Solutions Architect?. AWS Certified Solutions Architect Associate - Training Notes (eBook) Download this eBook (in PDF format) for the SAA-C02 with 300 pages of detailed facts, tables and diagrams. 14 AWS Config provides.
Elastic Container Service (ECS) Fargate Container Instances:. The AWS Cloud computing is increasing in a rapid manner from the past few years. With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs.
In this blog, we will help you prepare for the AWS Solution Architect Associate Certification Exam, give you some facts and summaries, provide AWS Solution Architect Associate Top 65 Questions and Answers Dump. The AWS Architecture Center provides reference architecture diagrams, vetted architecture solutions, Well-Architected best practices, patterns, icons, and more. The course includes many visual slides to help you understand the concepts.
In particular, it offers an outline as well as detailed lectures on all the objectives of SAA-C02. Getting Started with AWS CloudHSM Set up your environment Create your VPC, Subnets, IAM roles and security group. AWS and AWS Marketplace partners offer a variety of solutions for protecting sensitive data within the AWS platform, but for some applications and data subject to contractual or regulatory mandates for managing cryptographic keys, additional protection may be necessary.
Important When you create a cluster, AWS CloudHSM creates a service-linked role named AWSServiceRoleForCloudHSM. KMS is an AWS managed service for Cloud consumers that allows handling select key management lifecycle processes and facilitates symmetric key operations for encrypting data particularly encrypting AWS Block Volumes (EBS), Simple Storage Service (S3) Buckets, encrypting Redshift Data warehouses, Databases residing in Relational Database Service (RDS), Data stores in Elastic MapReduce (EMR). AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud.
In AWS CloudHSM, you create and manage HSM clusters, including creating users and setting their permissions. It cannot be arbitrarily designed. Both services offer a high level of security for your cryptographic keys.
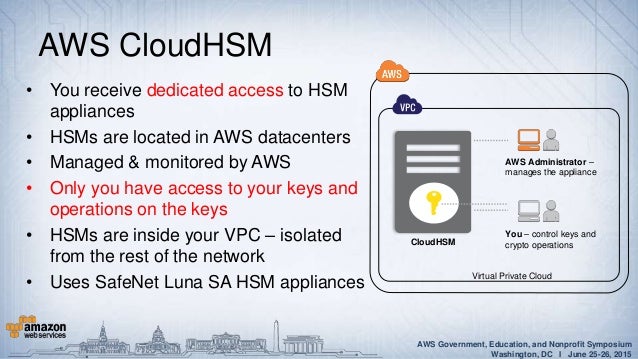
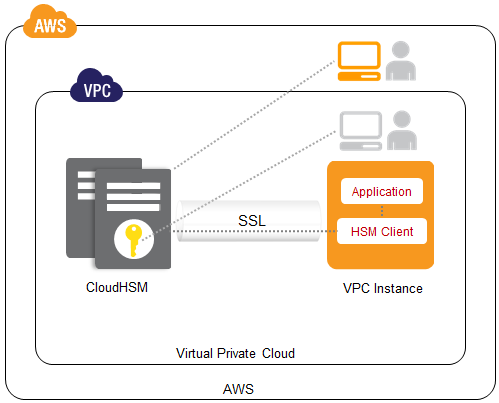
AWS CloudHSM provides a dedicated, FIPS 140-2 Level 3 HSM under your exclusive control, directly in your Amazon Virtual Private Cloud (VPC).". Enterprise architecture guides organizations in the delivery of the target production landscape to realize their business vision in the cloud. Architecture To communicate with your AWS CloudHSM instance, AWS puts an Elastic Network Interface (ENI) in a subnet inside your AWS account.
This is the official Amazon Web Services (AWS) documentation for AWS CloudHSM, a web service that provides cost effective hardware key management at cloud scale for sensitive and regulated workloads. CloudHSM offers you the flexibility to integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries. The AWS CloudHSM service helps you meet corporate, contractual and regulatory compliance requirements for data security by using dedicated Hardware Security Module (HSM) instances within the AWS cloud.
You will master AWS architectural principles and services such as IAM, VPC, EC2, EBS and elevate your career to the cloud, and beyond with this AWS solutions architect course. In this course, you’ll learn everything you need to know to ace your AWS Certified Solutions Architect Associate exam. Amazon Confidential and Trademark 自己紹介 髙橋悟史(たかはしさとし).
The AWS Solutions Architect Associate exam consists of 65 multiple-choice, multiple-answer questions. You have 130 minutes to complete the exam. Amazon Web Services (AWS) was launched in 06, and has since become one of the one of the most popular cloud platforms currently available in the market.
AWS service Azure service Description;. Amazon Web Services – Security of AWS CloudHSM Backups Page 1 Introduction Amazon Web Services (AWS) offers two options for securing cryptographic keys in the AWS Cloud:. The AWS CloudHSM service provides single-tenant access to each HSM within an Amazon Virtual Private Cloud (VPC).
AWS CloudHSM provides a managed hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. Your AWS Cloud architecture design needs to be well thought out because it forms the backbone of a vast network. You also create the symmetric keys and asymmetric key pairs that the HSM stores.
Please note that unlike the real AWS Solutions Architect exam, this free sample quiz is not timed – so you can take as much time as required to answer each question. Abstract This whitepaper outlines AWS practices and services that support enterprise architecture (EA) activities. It is written for IT leaders and enterprise architects in large organizations.
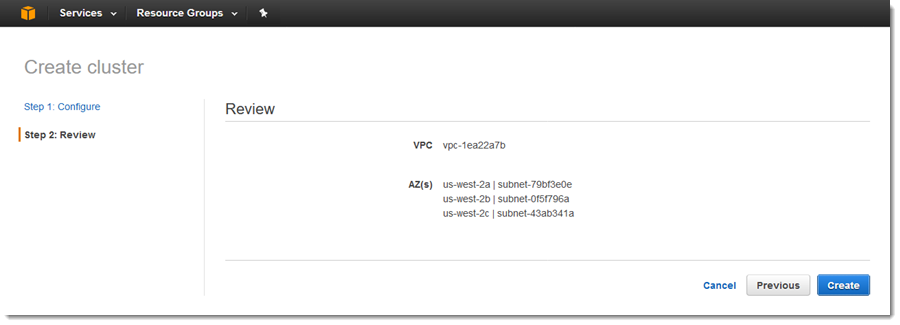
Click on the Create cluster button on the upper left-hand of the console which bring you to the Create cluster wizard. As an AWS customer, you benefit from a data center and network architecture that is built to meet the requirements of the most security-sensitive organizations. With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs.
The AWS Certified Solutions Architect - Associate video course is a vital tool to prepare for your SAA-C02 upcoming certification assessment. AWS CloudHSM creates a security group that allows inbound and outbound communication between HSMs in your cluster. In an AWS CloudHSM cluster, AWS CloudHSM keeps the keys on the individual HSMs in sync.
Azure Container Instances is the fastest and simplest way to run a container in Azure, without having to provision any virtual machines or adopt a higher-level orchestration service. © 19, Amazon Web Services, Inc. AWS Certified Solutions Architect Professional CloudHSM It is a cloud-based hardware security module (HSM) enables you to easily generate and use own encryption keys on the AWS.
The ENI can interact with the HSM residing in a separate VPC in an AWS account that is owned by AWS CloudHSM. AWS CloudHSM provides hardware security modules in the AWS Cloud. Apply to Software Architect, Cloud Engineer, Aws Consultant and more!.
CloudHSM offers you the flexibility to integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries. This whitepaper also provides in-depth information on how backups are protected in all three phases of the CloudHSM backup lifecycle process:. To keep the users and policies on each HSM in sync, update the AWS CloudHSM client configuration file before you manage HSM users.
In my example architecture, I’m using KSM with AWS managed CMKs to encrypt data-at-rest stored in RDS and EFS. CloudHSM's design features, integration with Amazon web services, CloudHSM monitoring, CloudHSM versus KMS, provisioning a CloudHSM, and CloudHSM costs. Creation, Archive, and Restore.
Then it logs into the key AWS CloudHSM client in the cluster using the credentials of a dedicated crypto user in the cluster. 11 AWS PrivateLink securely connects a VPC to supported AWS services. The AWS CloudHSM service helps you meet corporate, contractual, and regulatory compliance requirements for data security by using dedicated Hardware Security Module (HSM) instances within the AWS cloud.
We start by creating a CloudHSM cluster using the AWS CloudHSM console. These cheat sheets contain everything you need to know to fast-track your exam success. Cryptsoft CloudHSM® encapsulates Cryptsoft's experience in the key management and security market space and can be deployed into almost any environment with the ability to enhance, integrate with, or replace existing standards based or proprietary solutions.
For more information, see Cluster Architecture. You don't need to do anything to synchronize the keys on your HSMs. When you create an HSM, AWS CloudHSM put an elastic network interface (ENI) in your subnet so that you can interact with your HSMs.
Use the practical exercises to learn how to architect and build applications on Amazon Web Services. Depending on your requirements, it might be necessary to use AWS CloudHSM to protect your master keys. 12 13 AWS Shield protects against DDoS attacks.
CloudHSM is a device only available in the following 11 regions at this time. Appian Cloud instances will communicate with this VPC via an IPsec VPN tunnel. AWS and AWS Marketplace partners offer a variety of solutions for protecting sensitive data within the AWS platform, but for some applications and data subject to contractual or regulatory mandates for managing cryptographic keys, additional protection may be necessary.
AWS CloudHSM synchronizes the HSMs in each cluster so that they function as a logical unit. "AWS Key Management Service (KMS) is a multi-tenant, managed service that allows you to use and manage encryption keys. AWS CloudHSM is a security service that offers isolated hardware security module (HSM) appliances to give customers an extra level of protection for data with strict corporate, contractual and regulatory compliance requirements.
CloudHSM is customer-owned and managed. Compliance, Cloud Security Architecture, third-party security tools/platforms, encryption/KMS/CloudHSM, Inspector, Macie, IAM policies/roles, Shield, WAF, etc. CloudHSM has no upfront costs and provides the ability to start and stop HSMs on-demand, allowing you to provision capacity when and where it is needed quickly and cost-effectively.
And we'll cover how the CloudHSM device works to protect your crypto keys, I will cover how to monitor the CloudHSM appliance, and how to leverage Cloud Shield to ensure encryption is used. Each custom key store is associated with an AWS CloudHSM cluster in your AWS account. Cloud security at AWS is the highest priority.
Some practical information that is interesting to know when you plan to schedule the exam:. Platforms Available on the following Cloud Platforms:. AWS CloudHSM is a cloud-based hardware security module (HSM) that allows you to easily add secure key storage and high-performance crypto operations to your AWS applications.
AWS KMS is a managed service that uses hardware security modules (HSMs) to protect the security of your encryption keys. Solution architecture is a practice of defining and describing an architecture of a system delivered in context of a specific solution and as such it may encompass. Learn about AWS architectural principles and services like IAM, VPC, EC2, EBS and more with the AWS Solutions Architect Course.
A good AWS cloud architecture design should take advantage of some of the inherent strengths of cloud computing – elasticity, ability to automate infrastructure management etc. The new AWS CloudHSM offering is now a fully managed service from Amazon that has achieved full FIPS 14-2 level 3 compliance certification enabling it to be used in the U.S government and. CloudHSM is an important building block of Snowflake’s security infrastructure, ensuring the security.
S3 contains publicly available files only. CloudHSM is a hardware security module (HSM) that allows you to securely store keys and perform cryptographic operations on the device. AWS Key Management Service (AWS KMS) and AWS CloudHSM.
Explanation AWS CodeCommit is a fully-managedsource control service that hosts secure Git-based repositiories AWS CodeStar enables you to quickly develop, build, and deploy applications on AWS AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS(Amazon Web. Select Version AKO 0.9 .1 18.2 18.1 17.2 17.1 16.3. For the purposes of this whitepaper, we assume that you have a basic understanding of AWS CloudHSM and cluster architecture.
This expert guidance was contributed by AWS cloud architecture experts, including AWS Solutions Architects, Professional Services Consultants, and Partners. At a high-level, an AWS Solutions Architect’s primary duty is to deploy applications to infrastructure in the AWS cloud. GovCloud provides three AWS availability zones, allowing users to set up a high availability architecture similar to other regions, but without multi-region redundancy.
AWS Cloud Integration layer VPC Service logs are collected in Amazon S3 and analyzed and monitored using Amazon Elasticsearch. When you connect the custom key store to its cluster, AWS KMS creates the network infrastructure to support the connection. AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud.
With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. Amazon Web Services (AWS) certification training is essential for every aspiring AWS certified solutions architect. CloudHSM only operates in a VPC, so if you are still using AWS classic, you will need to migrate those instances to a VPC prior to connecting with the CloudHSM.
This free AWS practice quiz consists of questions with a mix of questions on core AWS services, including EC2, VPC and EMR. Therefore I’m not encrypting that data at all. The on-demand and reserved pricing models used in the rest of the Amazon cloud are also available in GovCloud, however, pricing may differ from that offered in regular AWS.
Open Banking on AWS 1 Implement the right architecture for Open APIs. For cluster configuration, we need to select a VPC and either select existing private subnets or create new private subnets. When you use an HSM from AWS CloudHSM, you can perform a variety of cryptographic tasks:.
It has come up with high-performance scalability, reliability, agility and responsibilities with certain design principles to run AWS on system efficiency. A hardware security module (HSM) is a computing device that processes cryptographic operations and provides secure storage for cryptographic keys. Then, create your cluster.
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog

Aws Privatelink Integration With Appian Cloud Appian 3

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog
Aws Cloudhsm Architecture のギャラリー

Vpc Noise

How To Run Aws Cloudhsm Workloads On Aws Lambda Aws Security Blog

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Terabitweb Blog

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
2
Protecting Your Data With Aws Kms And Aws Cloudhsm

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Terabitweb Blog

How Secure Is Amazon S Key Management Service Aws Kms Interconnections The Equinix Blog
Aws Cloudhsm Secure Key Storage And Cryptographic Operations Aws News Blog
Hashicorp Aws Integrating Cloudhsm Vault Enterprise
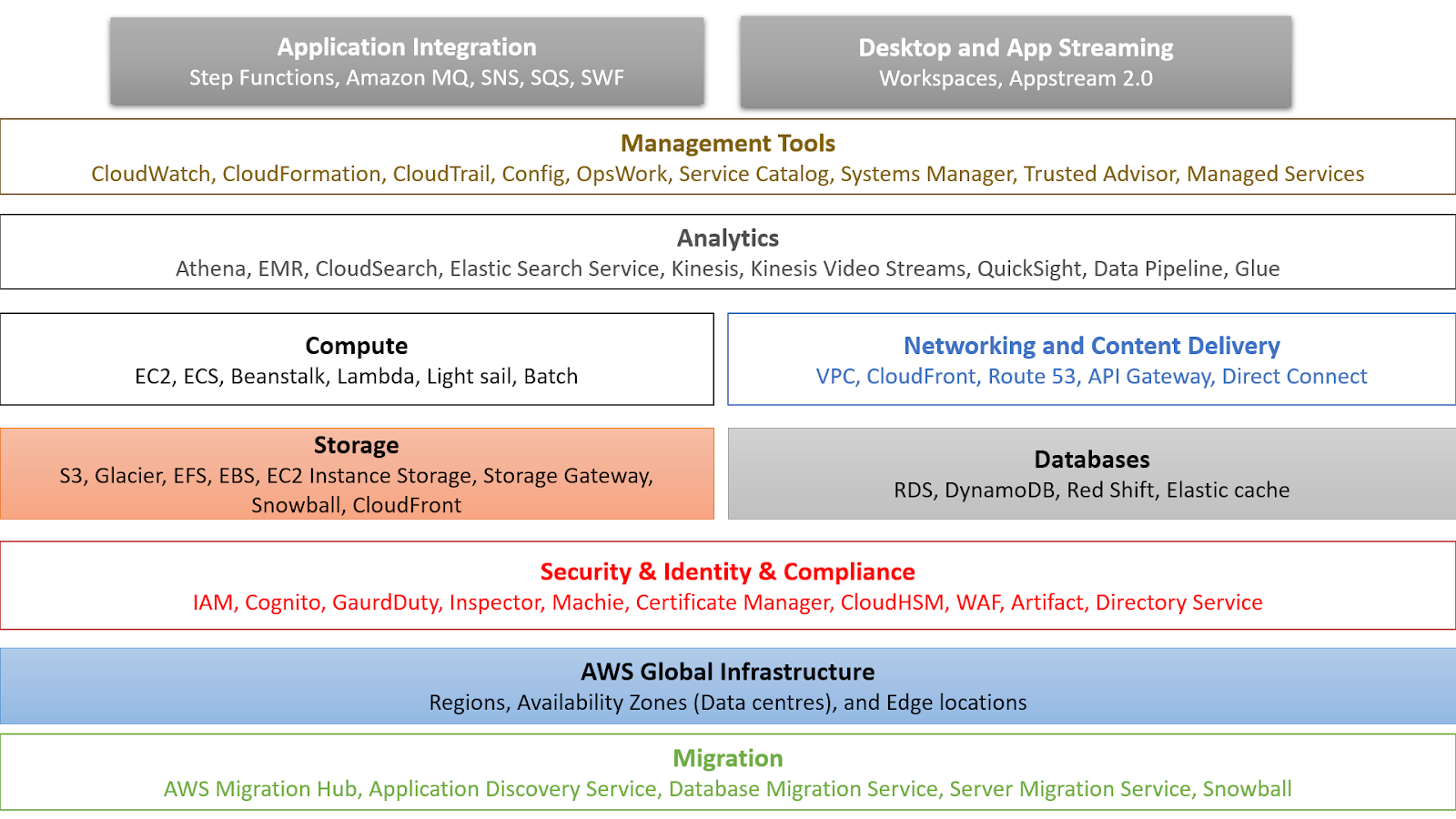
Aws Associate Architect Summary Of Services

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog

Aws Cloudhsm

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
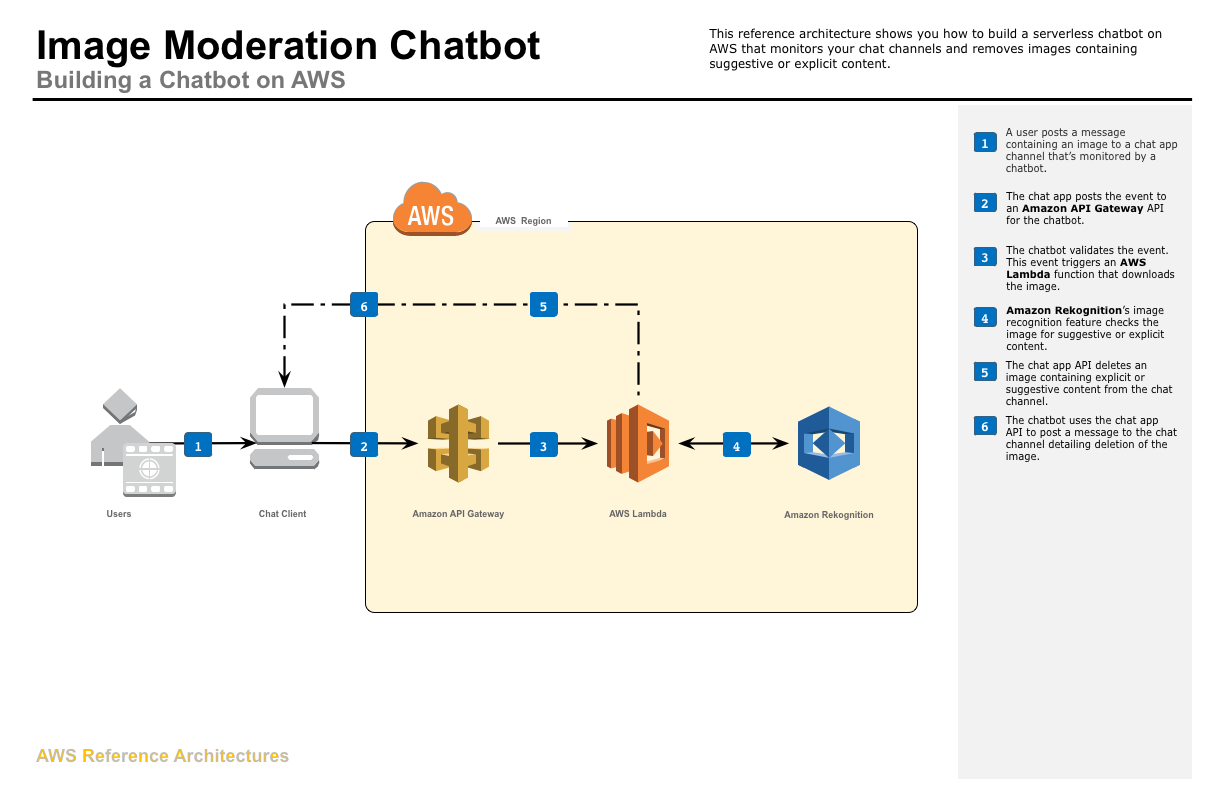
Aws Startup Architecture Of The Year Challenge

A Look Inside Iqlusion S Cosmos Hub Validator Architecture
Www Cloudsec Com Hk Pdf A1600 Pdf

Utimaco Cryptoserver Cloud The Root Of Trust Hsm For The Cloud
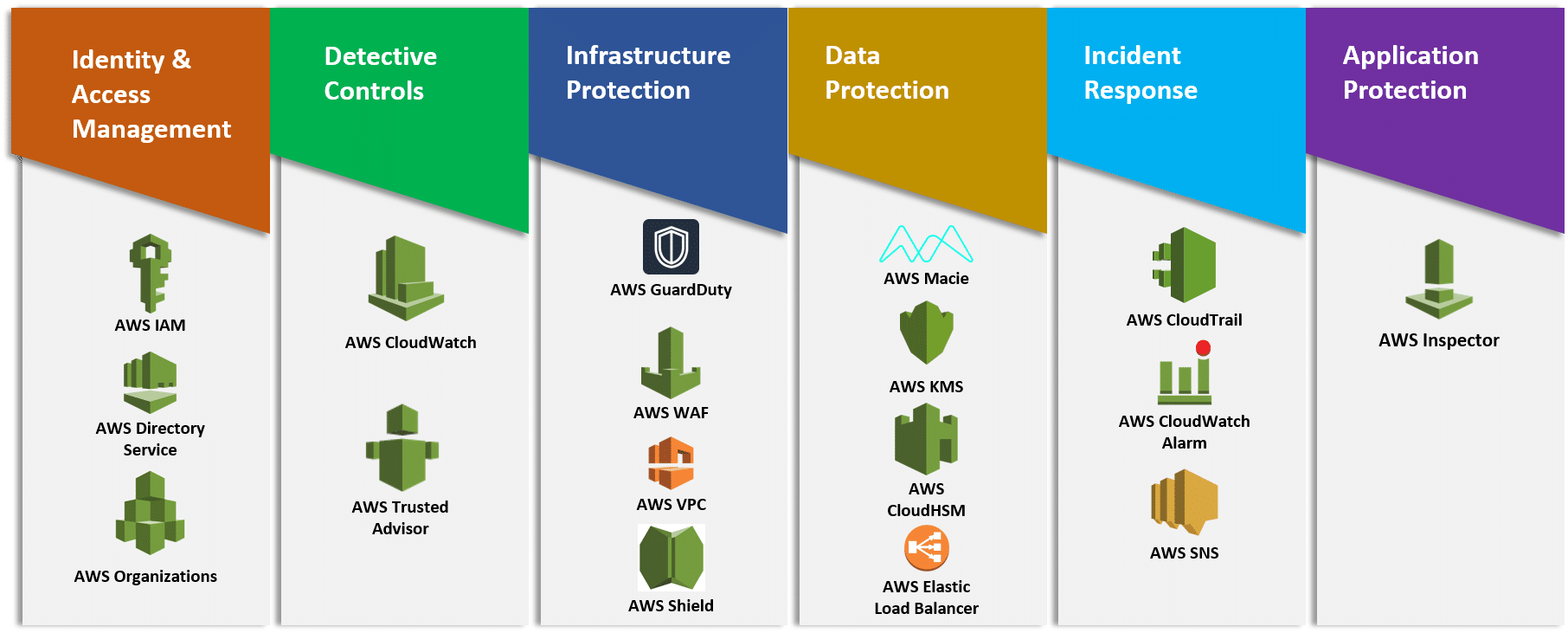
Aws Well Architected Framework Aws Ps

Vpc Noise

Ssl Noise
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads Aws News Blog

Security Iteanz Com

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Aws Cloudhsm Digital Cloud Training

Bring Your Own Key Byok Setup Process In Appian Cloud

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog

Aws Solution Architect Associate Certification Exam Questions And Answers Dump It Engineering Cloud Finance
Aws Certified Solutions Architect Professional Road Map Recording

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
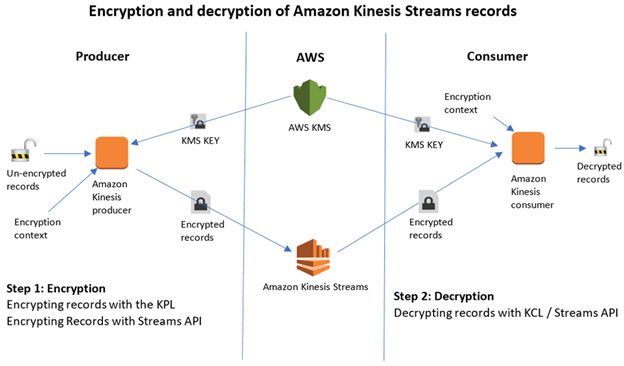
Aws Kms Testprep Training Tutorials

How To Remove Single Points Of Failure By Using A High Availability Partition Group In Your Aws Cloudhsm Environment Archives It Engineering Cloud Finance
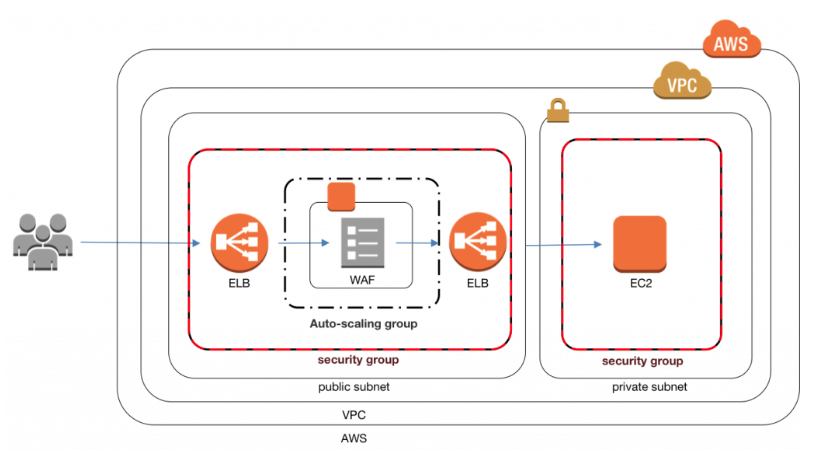
Protecting Your Data With Aws Kms And Aws Cloudhsm
Q Tbn 3aand9gcrbbeaol96hfrlu0ac03nvke7yh9m Igy14d Lreqxnwhhsx Vg Usqp Cau

3 Steps To Becoming An Aws Security Specialist Cloud Academy Blog
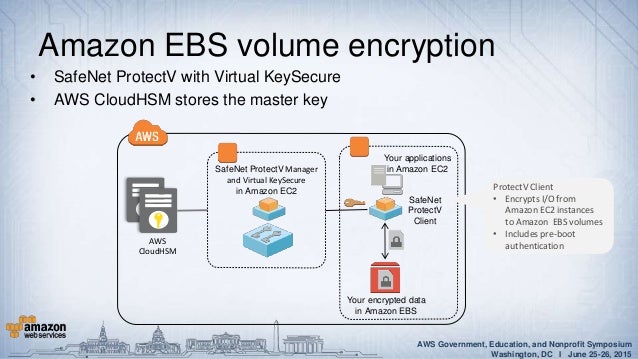
Aws Solutions Architect Aws Flashcards Memorang

Aws Architecture Diagrams Solution Aws Architecture Diagram Diagram Architecture Enterprise Application

Aws Cloudhsm

Bring Your Own Key Byok Appian 3

How To Remove Single Points Of Failure By Using A High Availability Partition Group In Your Aws Cloudhsm Environment Aws Security Blog
Cloud Netapp Com Hubfs Encryption white paper Netapp ultimate aws encryption guide Pdf T
Aws Certified Solutions Architect Professional Road Map Recording
2
Q Tbn 3aand9gcrlxba7bkwaafa6cdftw1ulp1zjtohzin X Wvgxcexhov7eqm Usqp Cau

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
Help Ssh Com Support Solutions Articles Architecture Blueprint Amazon Web Services Deployment

How To Run Aws Cloudhsm Workloads On Docker Containers Aws Security Blog
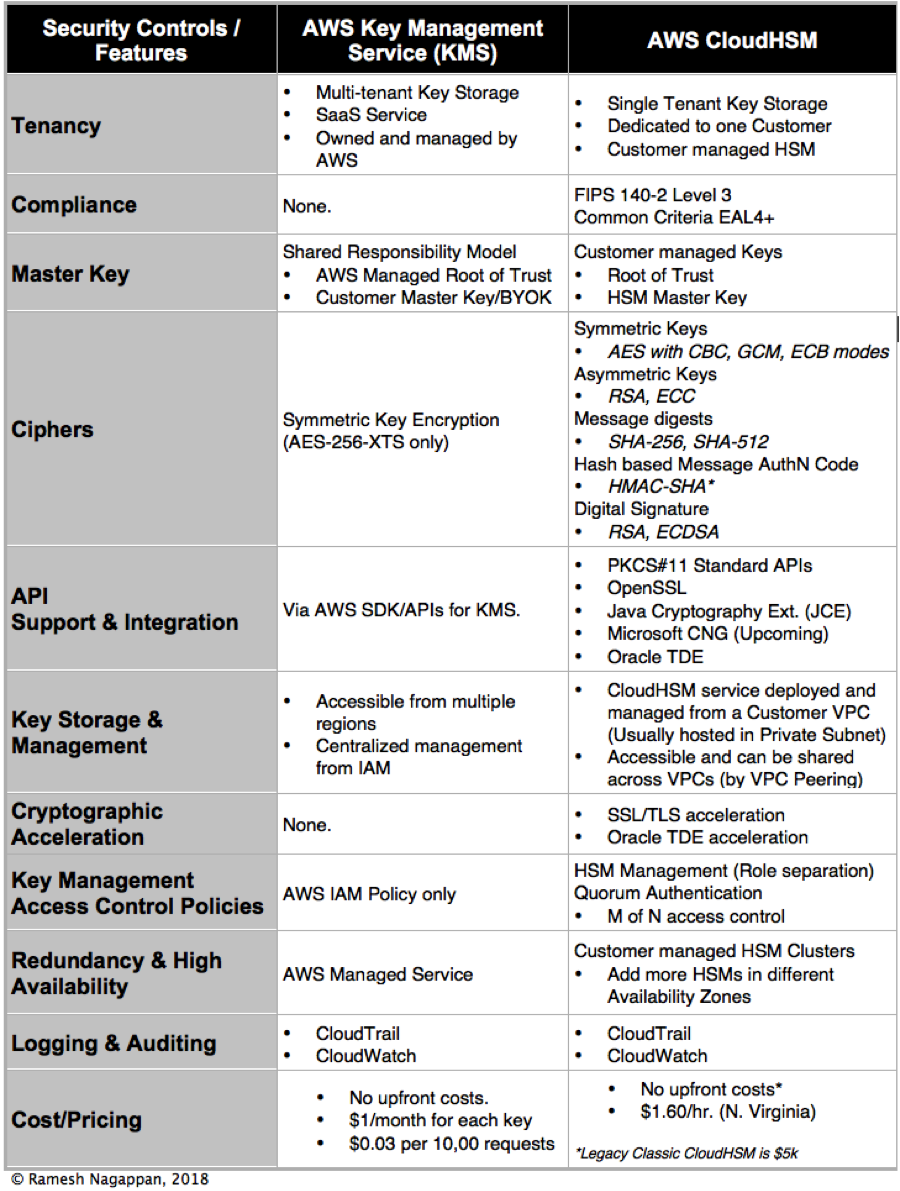
Encryption And Key Management In Aws Comparing Kms Vs Cloudhsm Web Security Patterns
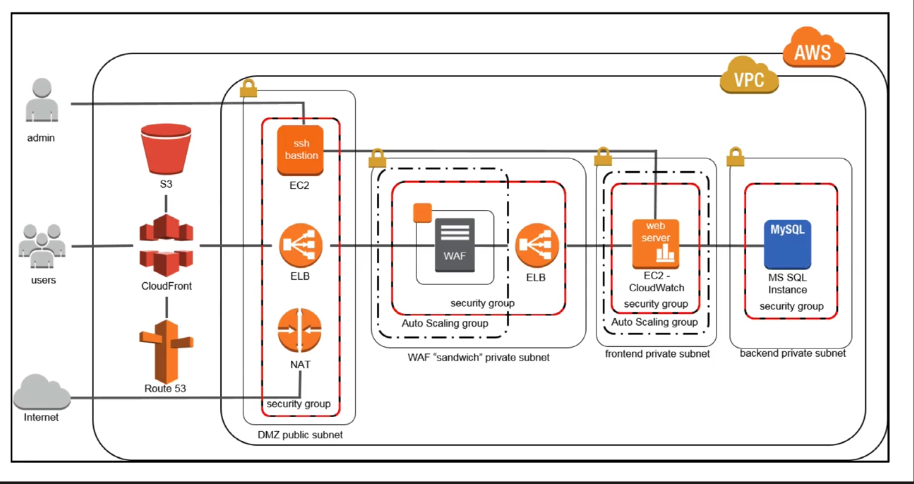
Architecting Your Healthcare Application For Hipaa Compliance Part 2 By Aws Startups Aws Startup Collection Medium
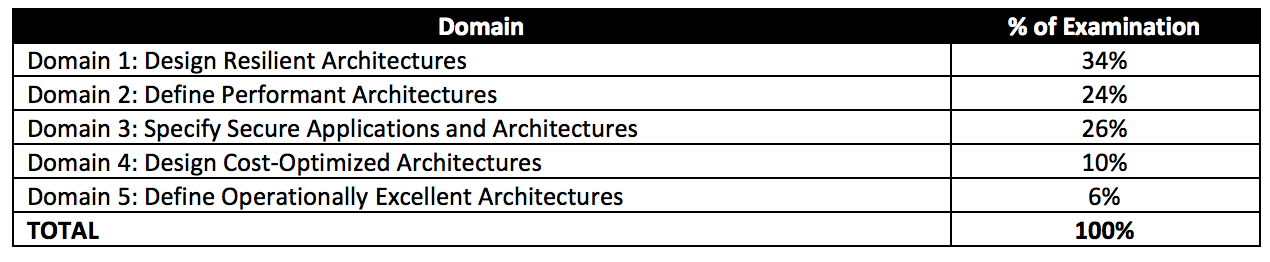
Aws Certified Solutions Architect Associate Saa C01 Exam Learning Path Obsolete Jayendra S Blog

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
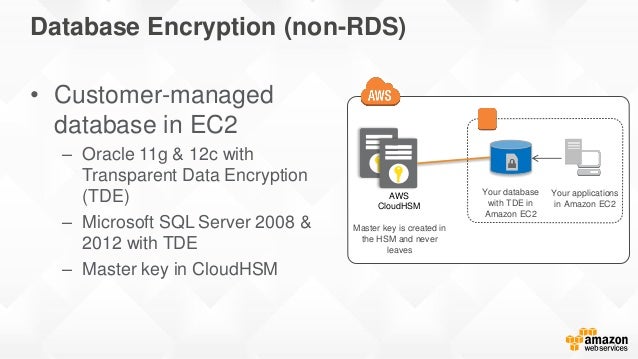
Deep Dive Aws Cloudhsm Classic
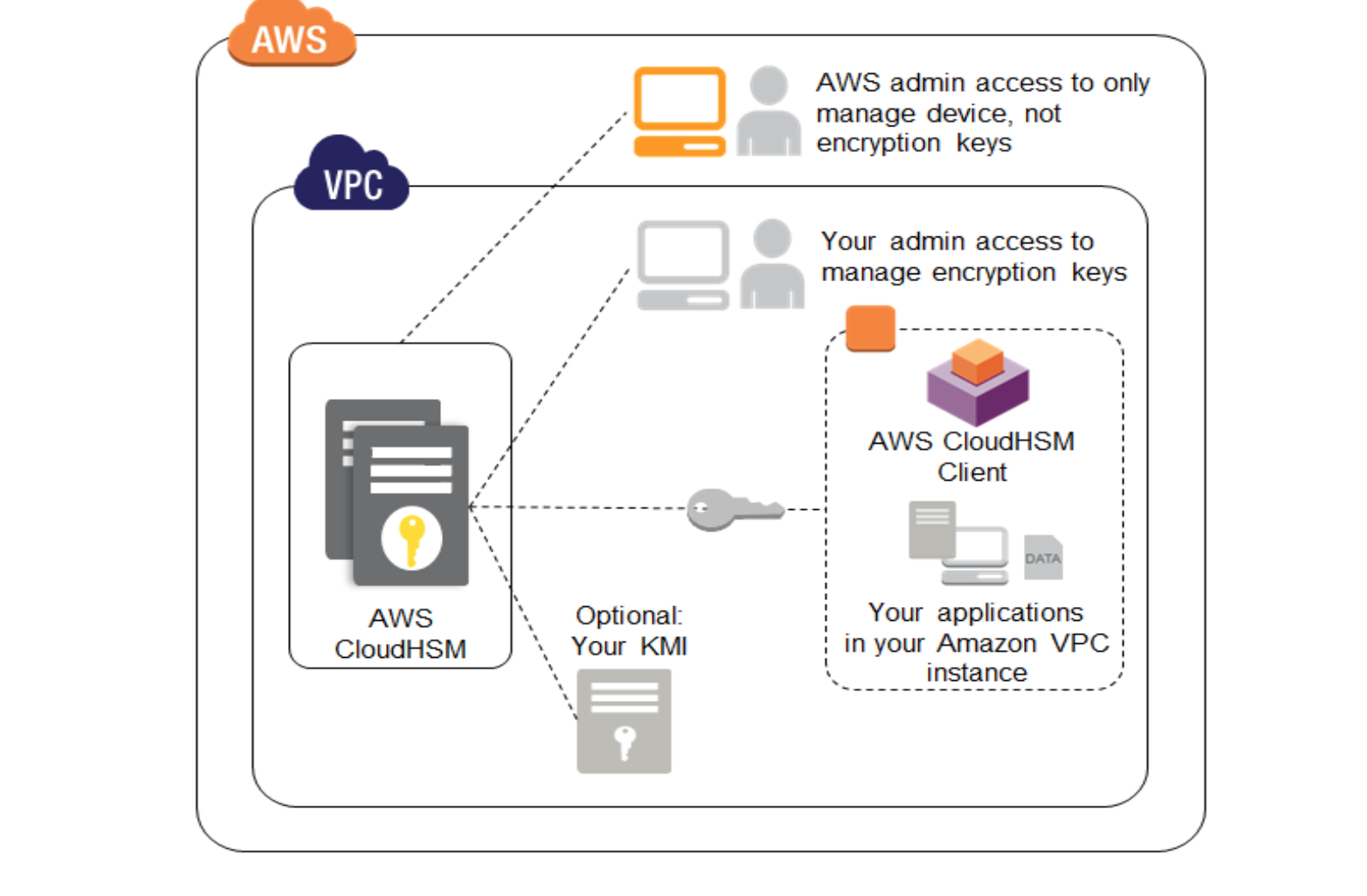
Aws Encrypting Data At Rest Whitepaper Certification Jayendra S Blog
Q Tbn 3aand9gcrbbeaol96hfrlu0ac03nvke7yh9m Igy14d Lreqxnwhhsx Vg Usqp Cau

Signing Executables With Microsoft Signtool Exe Using Aws Cloudhsm Backed Certificates Terabitweb Blog
Aws Certified Solutions Architect Associate Saa C02 Learn Cantri

Vpc Noise

Amazon Web Services Security Overview Webstep No
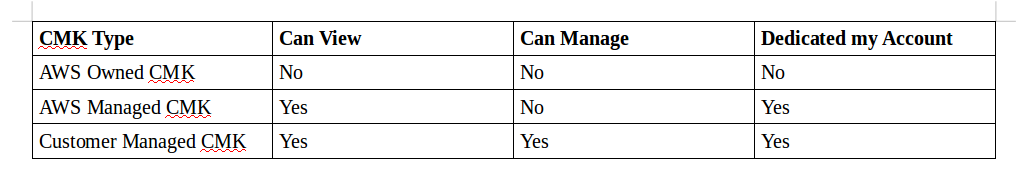
Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium
3

Using Aws Cloudhsm In High Availability Mode

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
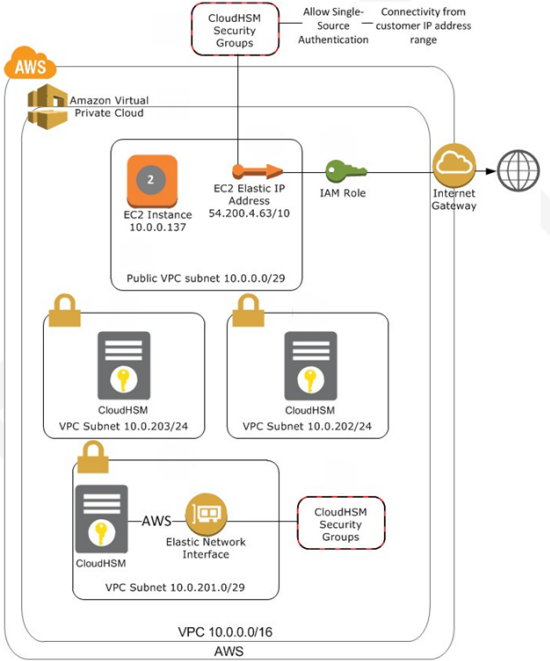
Aws Cloudhsm Update Aws News Blog
Aws Launches Cloudhsm App To Bolster Data Security In The Cloud Siliconangle
Devops And Cyber Security In Aws Devsecops By Joshua G Edwards Medium

Aws Cloudhsm
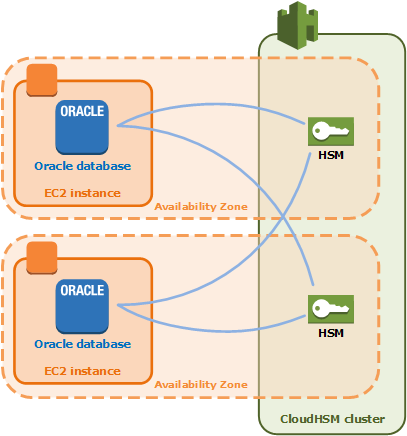
Aws Cloudhsm Clusters Aws Cloudhsm

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog
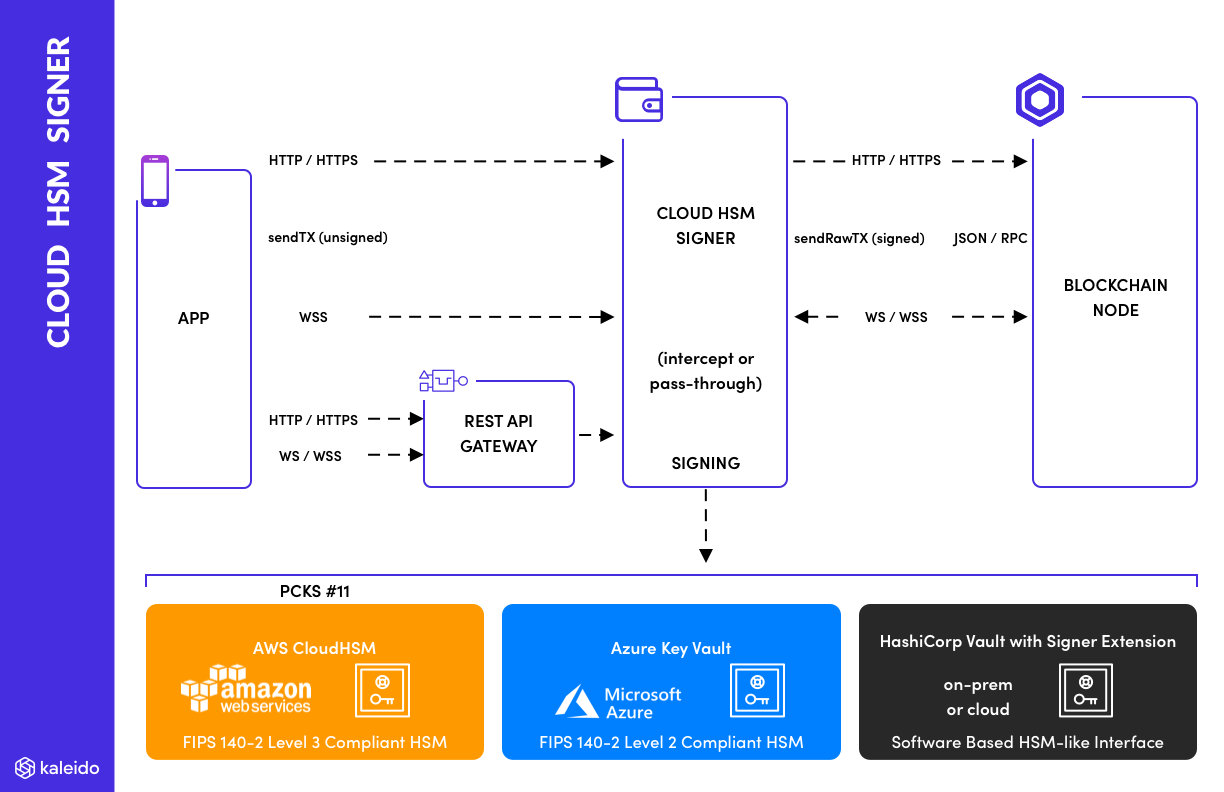
Introduction Knowledge Center

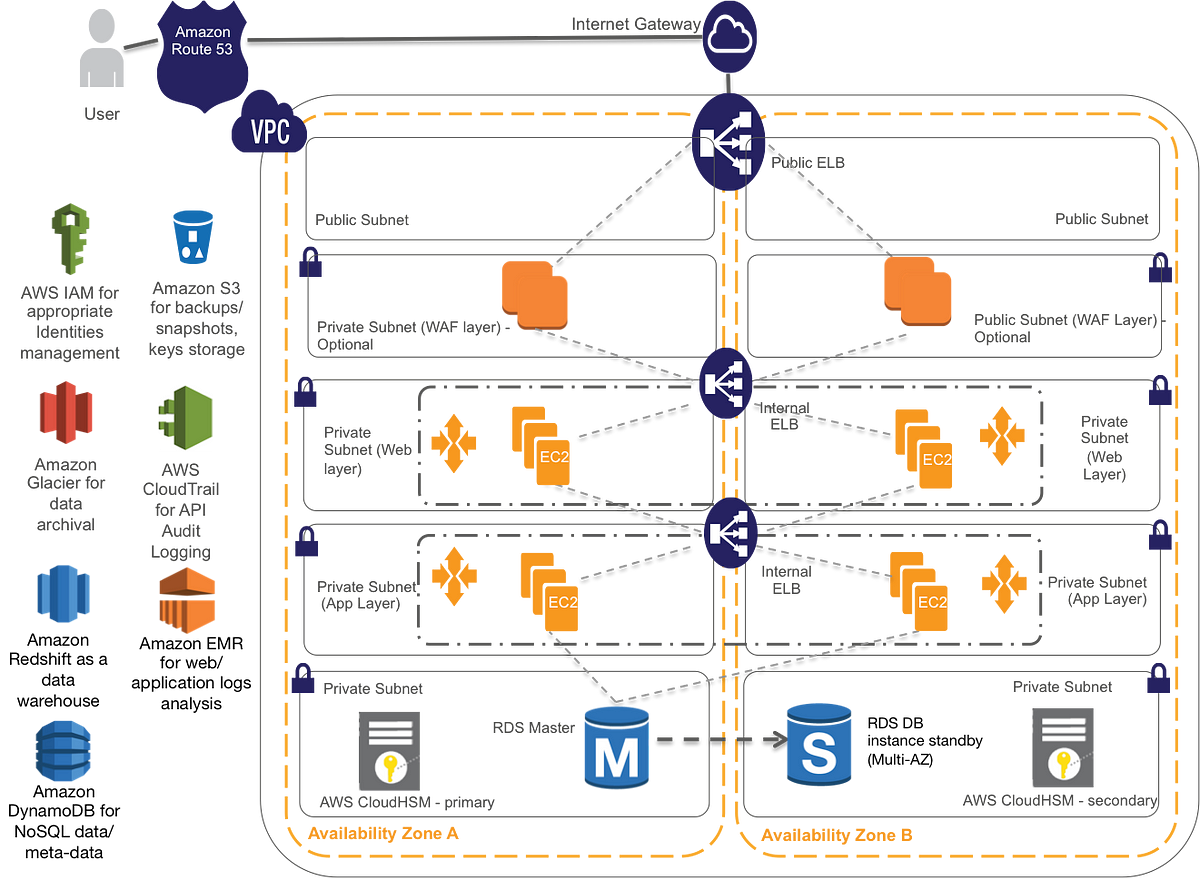
Architecting Hipaa In The Cloud Using Aws
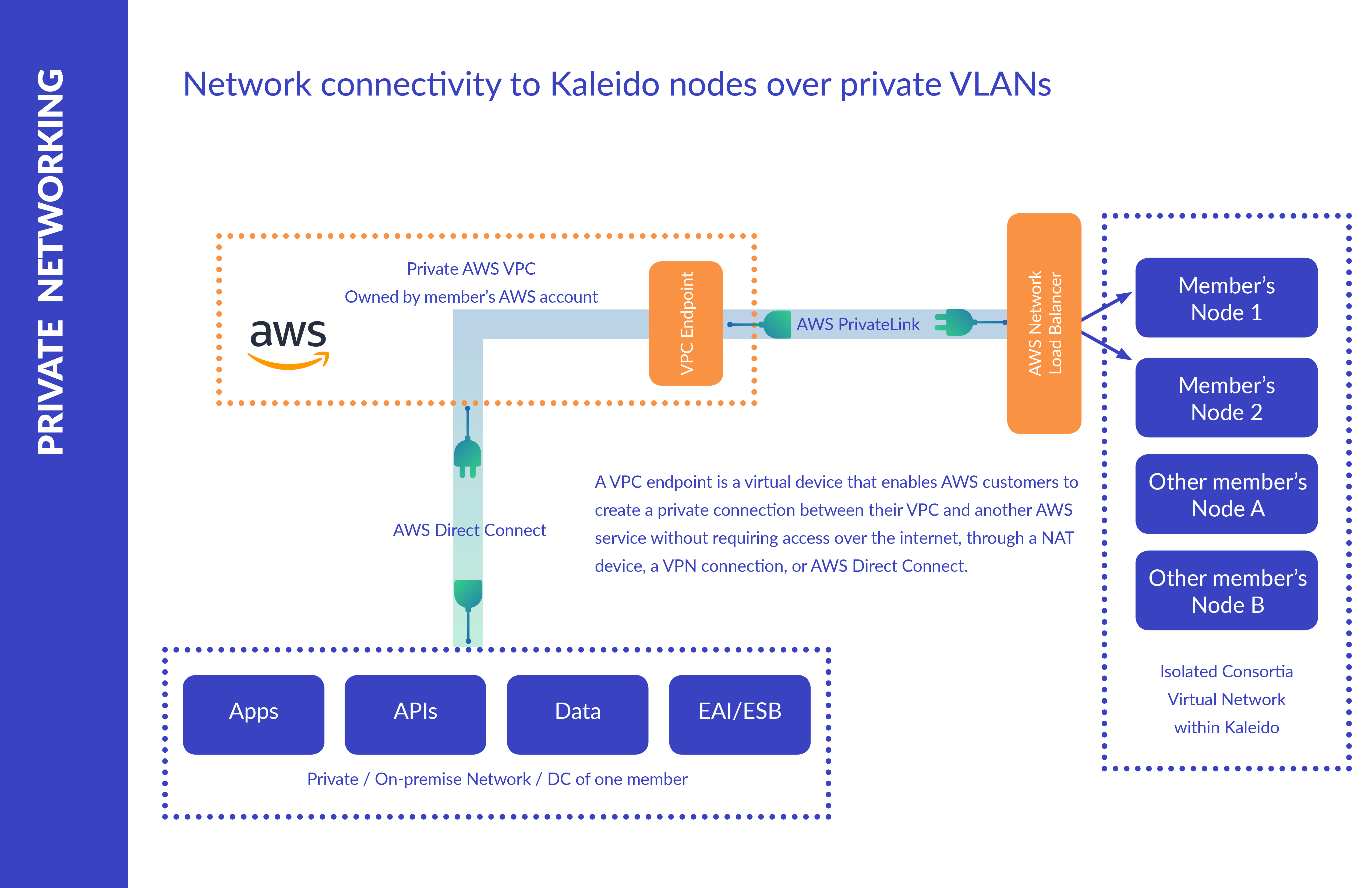
Advanced Private Networking Knowledge Center
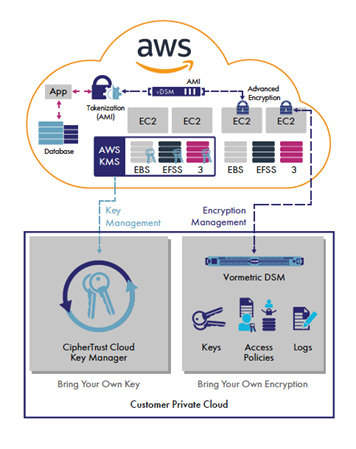
Advanced Encryption Solutions For Amazon Web Services Thales

Aws Cloudhsm Aws Security Blog
2

Aws Cloudhsm
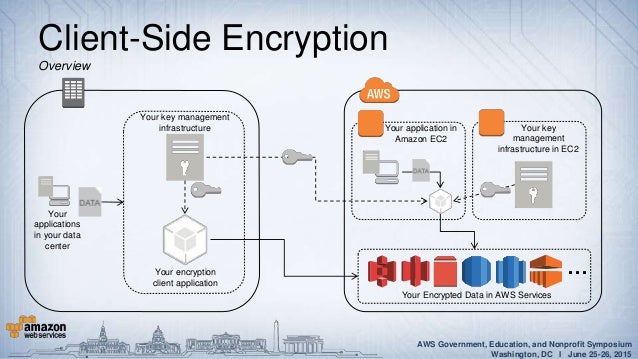
Protecting Your Data With Aws Kms And Aws Cloudhsm

Vpc Noise

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog
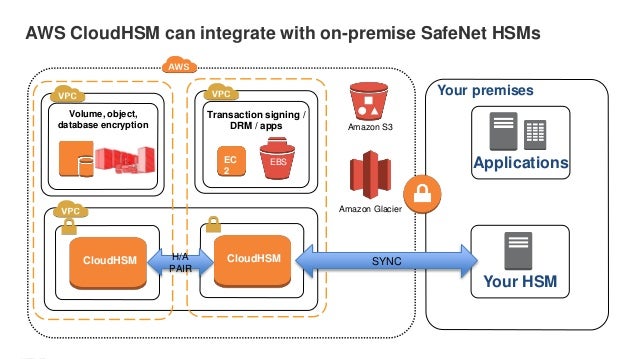
Day 4 Securing Your Business On The Aws Cloud

Solution Technical Overview
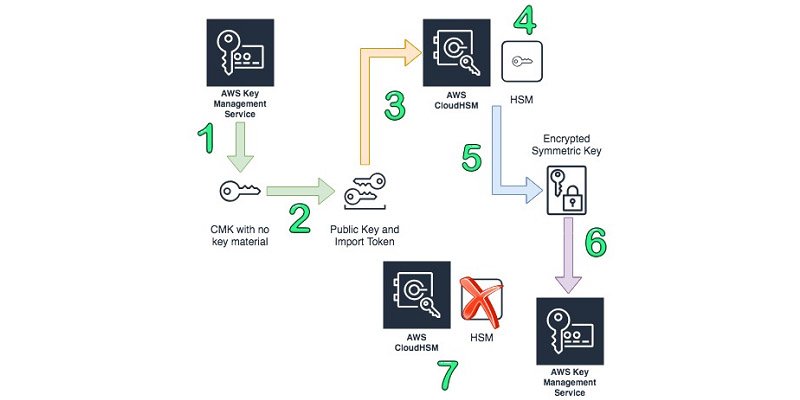
Aws Security Learn How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm T Co 7sqet0fexu T Co Doxri2iani

Why Would You Deploy Your Pki In The Cloud Primekey

July Latest Braindump2go Saa C02 Pdf And Vce Dumps Free Share 252 262 By Ruth Griffith Free Dumps Issuu

Aws Cloudhsm Aws Architecture Blog
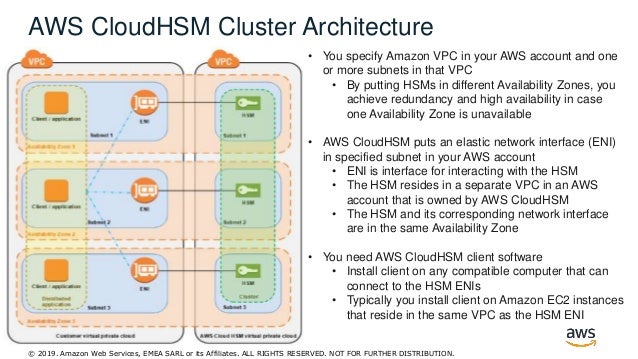
Aws Security Webinar The Key To Effective Cloud Encryption
D1 Awsstatic Com Whitepapers Establishing Enterprise Architecture Pdf

Aws Services Aws Pro Cert

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Aws Security Blog
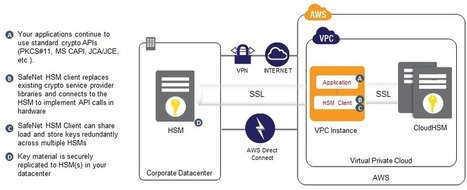
Aws Cloudhsm Dedicated Hardware Security Modu

Aws Advanced Technology Partner Modo

Top 14 Must Haves For Your Aws Architecture Checklist Cloudcraft Blog
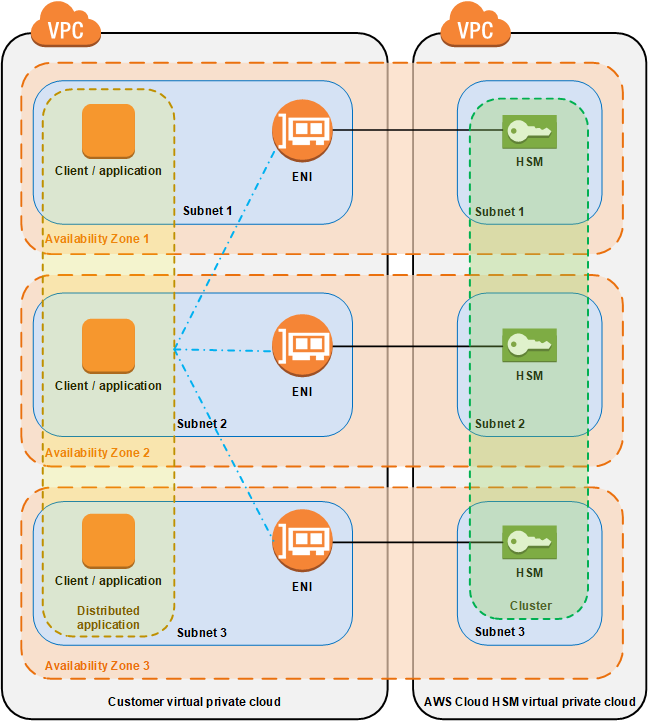
Aws Cloudhsm Clusters Aws Cloudhsm

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Aws Security Blog

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
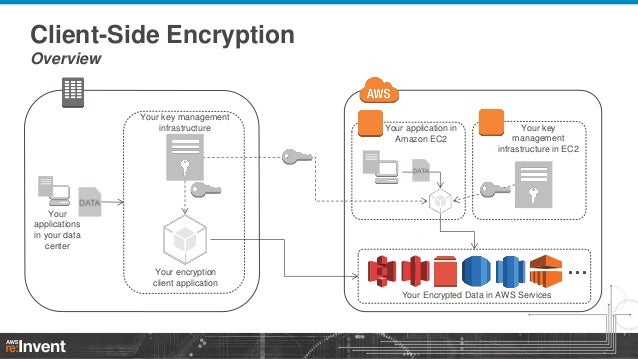
Encryption And Key Management In Aws Sec304 Aws Re Invent 13
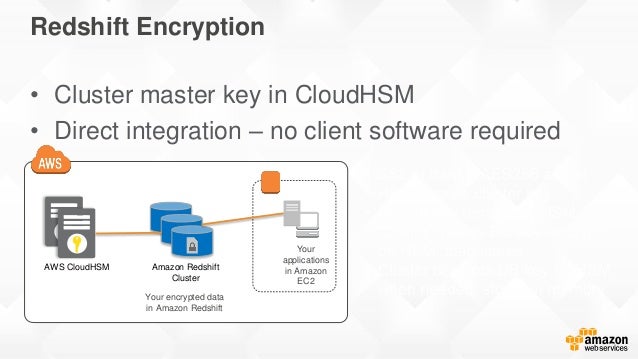
Deep Dive Aws Cloudhsm Classic

Migrating From A Aws Cloudhsm Classic Partition

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog

Bring Your Own Key Byok Appian 3

Aws Iam Digital Cloud Training



