Aws Cloudhsm Logo
Cloud Security with AWS and Microsoft Azure - In this course, we would explore Cloud security tools, services and options on Microsoft Azure and Amazon Web Services (AWS).
![]()
Aws cloudhsm logo. Monitor types and attributes Amazon Cloud HSM (AWS_CLOUDHSM_CLUSTER). In a single dashboard, you have visibility and over your entire cloud perimeter and the ability to drill down into any event. This name must be unique within your AWS account, can have a maximum of 32 characters, must contain only alphanumeric characters or hyphens, and must not begin or end with a hyphen.
I was dorking around with AWS (and related services), hoping that I could stay in the Free Tier, like I do when I'm exploring Google App Engine. AWS KMS CMKs are backed by FIPS-validated hardware service modules (HSMs) that KMS manages. You could develop Mobile, Web, IoT, AI, and other applications.
With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. Well, we need a way to tell the system (a.k.a. Select Version AKO 0.9 .1 18.2 18.1 17.2 17.1 16.3.
The described workflow performs the following tasks in the AWS Cloud:. Amazon Web Services (AWS) Regions:. Partners/aws/ About AWS CloudHSM,.
Brands CM - CZ;. Expand here to see the solution ) Keep in mind that the KMS Custom Key Store functionality makes use of a minimum of two AWS CloudHSM instances. You would be in a position to take AWS Cloud Practitioner Exam and qualify with good marks.
It enables you to securely generate, store, manage, and protect encryption keys in a way that these keys are accessible only by you or authorized users that only. Encryption Encryption capabilities Key management options P AWS Key Management Service Hardware-based cryptographic key storage options P AWS CloudHSM. PMI-RMP®, PMI-PBA®, CAPM®, PMI-ACP® and PMI Registered Education Provider Logo are registered marks of the Project Management Institute, Inc.
Go pricing model similar to AWS cloud services. BMC PATROL for Amazon Web Services 2.1. AWS Trusted Advisor provides best practices in four categories:.
Associates the created AWS key pair and the security group with a previously imported EC2 instance, and launches this instance. It’s cloud computing platform which comprise more than 100 services. Helping to protect the confidentiality, integrity, and availability (CIA) of your systems and data is of the.
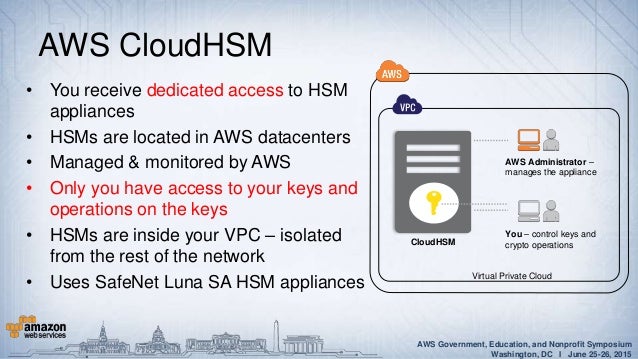
In this video, explore single-tenant HSM encryption key services. To manage your own HSMs, use AWS CloudHSM. AWS services are supported by a number of tried and true Amazon offerings that include Active Directory and AWS CloudHSM’s key storage, that enables you to easily generate and use your own encryption keys via the AWS Cloud.
AWS CloudHSM SafeNet KeySecure is the only solution to optionally provide a hardware root of trust for encryption keys in support of the AWS CloudHSM service, available directly from AWS. For a confirmation we probably would need access to the CloudHSM OpenSSL engine implementation. The AWS CloudHSM service uses SafeNet's tamper-resistant Luna® SA hardware security modules as its root of trust to provide customers with single-tenant appliances in the AWS cloud to meet their.
Volume_size - The size of the volume in gigabytes. Click here to view it. AWS Documentation Amazon CloudFront Developer Guide How you set up CloudFront to deliver content Amazon CloudFront is a web service that speeds up distribution of your static and dynamic web content, such as .html, .css, .js, and image files, to your users.
Having command over all the options, services and tools available. AWS Cloud Security LiveLessons explores Amazon Web Services (AWS), which offers a scalable cloud computing platform designed for high availability and reliability, providing the tools that allow you to run a wide range of applications. AWS' HSMs) about which key we are talking and OpenSSL doesn't support identifiers or handles natively with the CLI interface, so we need a work-around.
This is the backbone of the AWS system. SafeNet ProtectV with Virtual KeySecure is now available to run entirely on Amazon Web Services. It is a cloud-based hardware security module (HSM).
Use an AWS CloudHSM cluster with customer master keys. Learn about the pros and cons and explore the integration options with Key Management Service. AMAZON AWS ACCOUNTS WITH $5K & $10K CREDITS AVAILABLE What is Amazon AWS?.
From the Authentication section, provide the following parameters and click Save:. Brands AP - AZ;. Amazon Web Services offers reliable, scalable, and inexpensive cloud computing services.
Brands BA - BZ;. Implement better security controls for your resources in the AWS cloud. If you want to use asymmetric encryption, use AWS CloudHSM.
AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. May (5) April (9) March (2) February (1) January (1). Helping to protect the confidentiality, integrity, and availability (CIA) of your systems and data is of the.
PRINCE2® is a. AWS Certified Security Specialty Course. When using any AWS Mark (other than the Logo, with respect to which the formatting requirements are set forth in Section 8 below, or in a URL), you must distinguish the AWS Mark from the name of Your Content and/or other surrounding text by capitalizing the first letter of the AWS Mark, capitalizing or italicizing the entire AWS Mark, placing.
So first, why do we need a fake private key at all?. Only your organization has access to the keys stored in CloudHSM—AWS has no ability to view or access the keys. Learn More Engineered for the Most Demanding Requirements.
The FAQs states that the AWS CloudHSM provides a JCE (com.cavium.provider.caviumprovider). This means that you are granting Datadog read only access to your AWS data. Amazon AWS has several security products, such as a hosted Active Directory, AWS Identity Management, AWS Certificate Manager, and AWS CloudHSM.
Brands AA - AO;. Encrypted must be set to true when this is set. Access Control and Management UNIV/POLTEK.
Des Logos, für das die Formatierungskriterien in Abschnitt 8 festgelegt sind, oder in einer URL) nutzen, müssen Sie die AWS Marke vom Namen Ihres Inhalts und/oder vom umgebenden Text. Snapshot_id - The Snapshot ID to mount. On completion of this course you would be able to develop and deploy your applications over Amazon Cloud- Amazon Web Services.
Job function is a subset of AWS managed and is designed to align with common IT job functions. Name - (Optional) The name of the LB. T o store master key material and apply a routing to re-create a new key periodically and replace it in AWS KMS.
Our specialty training course covers a detailed overview of using AWS security services to stay secure on the AWS Cloud. It aggregates, analyzes, prioritizes information from across your other AWS and third-party cloud resources. Select Require external ID and enter the one generated in the AWS integration tile.Make sure you leave Require MFA disabled.For more information about the External.
The Authentication section in the AWS EVENTBRIDGE INTEGRATION screen appears. Creates the AWS key pair required for launching an AWS EC2 instance. AWS Security Hub is the seat of operations for Amazon Cloud Security.
Here is the snapshot of the exam blueprint. Cost optimization, security, fault tolerance, and performance improvement.You can use Trusted Advisor checks to monitor and improve the deployment of Amazon EC2, Elastic Load Balancing, Amazon EBS, Amazon S3, Auto Scaling, AWS Identity and Access Management, and other services. AWS CloudHSM is a cloud-based hardware security module that lets you generate and use your own encryption keys on the AWS cloud.
In AWS CloudHSM, you create and manage HSMs, including creating users and setting their permissions. Learn all the available Identity a. … If you run workloads that require … that additional level of compliance, … the only way to get there in AWS is with CloudHSM.
You create a template that describes all the AWS resources that you want (like Amazon EC2 instances or Amazon RDS DB instances. Create a new role in the AWS IAM Console.;. The BMC logo, and other BMC marks are.
This topic addresses the Data Security topic as highlighted in the AWS Blueprint for the exam guide. KMS allows you to gain more control for access to the data that you encrypt. AWS CloudHSM is a cloud-based dedicated, single-tenant HSM allowing you to include secure key storage and high-performance crypto operations to your applications on the AWS platform.
Brands 0 - 9;. AWS is infrastructure as a service. Number (#) Border range.
We can check the type from the console on the Policies page within IAM:. An AWS IAM policy's type can be either AWS managed, Job function, or Customer managed. AWS CloudFormation is a service that helps you model and set up your Amazon Web Services resources so that you can spend less time managing those resources and more time focusing on your applications that run in AWS.
Some of them include:. Use AWS security services such as AWS Identity and Access Management, Amazon Virtual Private Cloud, AWS CloudTrail, Amazon CloudWatch, AWS Key Management Service, AWS CloudHSM, AWS Config, AWS Service Catalog, and AWS Trusted Advisor;. Choosing a partnership with AWS for your enterprise IaaS needs offers several benefits including the following:.
Management Services & Options:. With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. For Account ID, enter (Datadog’s account ID).
It's DIY computing, which you can use for pretty much anything you use computers for. Identity and Access Management (IAM). What level of FIPS 140-2 cryptographic validation does the AWS KMS HSM hold?.
Creates a new security group in the AWS Cloud. Volume_type - The type of volume. AWS Systems Manager 37 Placement Groups 37 AWS Elastic Beanstalk 37 Amazon Elastic Container Service and AWS Fargate 38 AWS Lambda 38 VM Import/Export 38 Elastic Load Balancing and Auto Scaling 38 AWS CLI Example 39 Summary 40 Exam Essentials 40 Review Questions 42 Chapter 3 Amazon Simple Storage Service and Amazon Glacier Storage 47.
The following arguments are supported:. The current list of job functions includes Administrator, Billing, Database Administrator. If any of these requirements apply to you, consider using AWS CloudHSM with AWS KMS to create a custom key store.
In this article, we are writing about AWS Virtual Private Cloud (VPC) in Amazon Web Services (AWS). Create Aws Key Pair:. But I would like to use Sunpkcs11 provider for this.
AWS Security Identity & Compliance. Is it possible to use the Sunpkcs11 provider in combination with the AWS CloudHSM or am I limited to the Cavium provider in this regard?. Free to join, pay only for what you use.
AWS Pricing Calculator lets you explore AWS services, and create an estimate for the cost of your use cases on AWS. AWS Cloud Security LiveLessons explores Amazon Web Services (AWS), which offers a scalable cloud computing platform designed for high availability and reliability, providing the tools that allow you to run a wide range of applications. AWS KMS is a managed service that is integrated with various other AWS Services.
Brands CA - CL;. Can be "standard", "gp2", "io1" or "io2". You can use it in your applications to create, store and control encryption keys to encrypt your data.
AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. Refers to the Unique Identifier to access the AWS EventBridge. Launch clusters in private VPC subnets corporate data center Amazon S3 Data Scientists AWS region Business end users Private VPC subnet AWS CloudHSM AWS Direct Connect Enterprise data sources AWS KMS Amazon Redshift S3 VPC endpoint Amazon EMR Custer Public VPC subnet Internet Gateway VPC NAT Gateway Customer Gateway Virtual Private Gateway.
AWS Marketplace is a digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on AWS. AWS KMS only supports symmetric encryption. AWS CloudHSM allows users to store their encryption keys in hardware security modules (HSMs) that meet government standards for secure key management.
Atlantic.Net offers Robust Managed Personalized Security Solutions to make sure your data is always safe, including Managed Firewall, Managed Intrusion Prevention System, Trend Micro Deep Security, and. A few days ago, I get a letter from Amazon that they've charged me $33 or so for my 2 days of exploration. You also create the symmetric keys and asymmetric key pairs that the HSM stores.
Kms_key_id - The ARN of the AWS Key Management Service (AWS KMS) customer master key (CMK) to use when creating the encrypted volume. You will learn AWS recommended security practices, security features of AWS key services including compute, storage, networking, and database services. CloudHSM offers you the flexibility to integrate with your applications using industry-standard APIs.
This gives you greater control as AWS has no access … to the keys that you generate. Select Another AWS account for the Role Type.;.

Security Of Aws Cloudhsm Backups By Aws Whitepapers
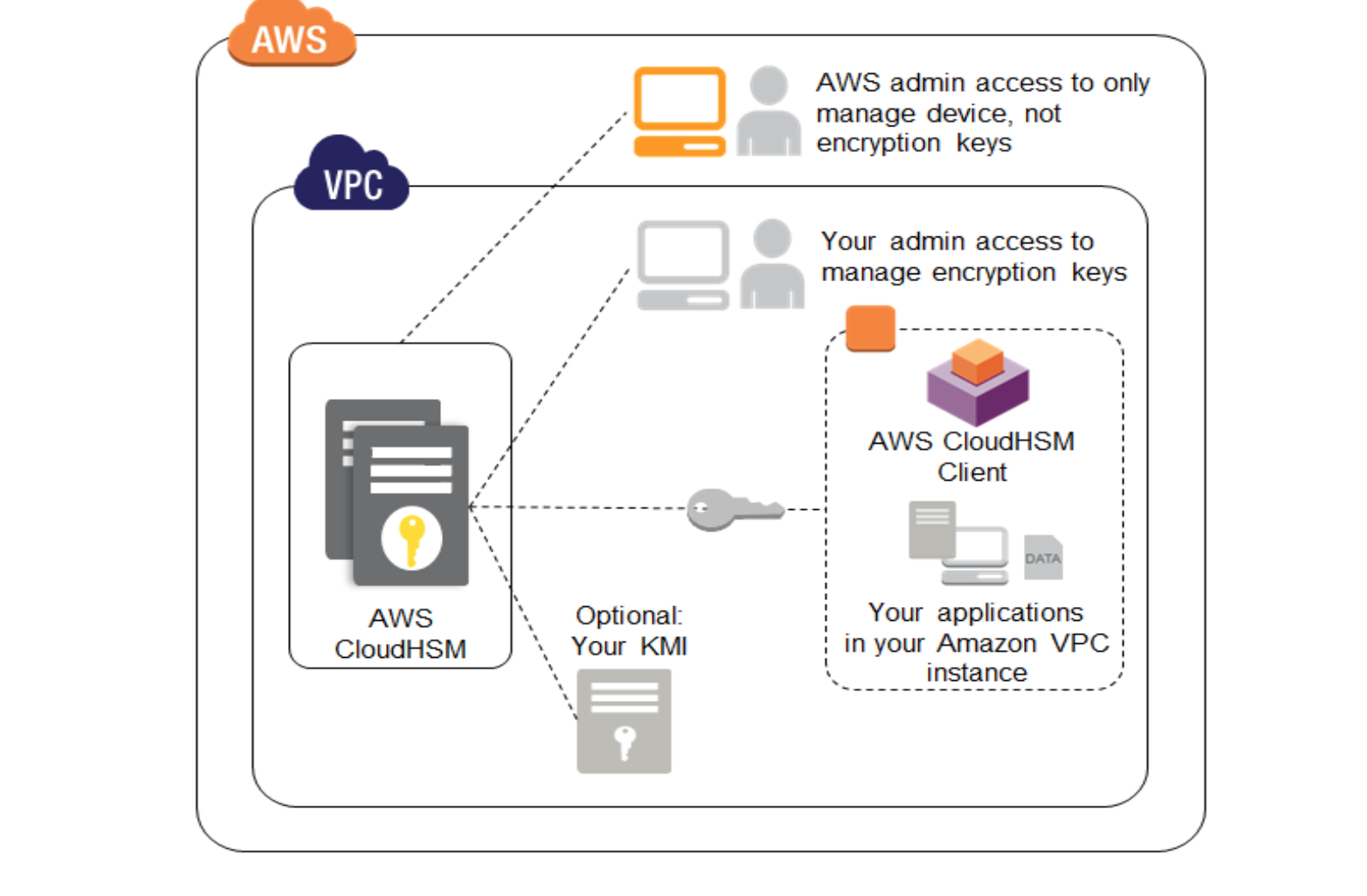
Aws Jayendra S Blog Page 11

From Amazon Web Services Cloudhsm Classic To Cloudhsm Blog
Aws Cloudhsm Logo のギャラリー

3 Steps To Becoming An Aws Security Specialist Cloud Academy Blog

Understand Cloudhsm

Features Aws Cloudhsm Amazon Web Services Aws
Aws Launches Cloudhsm App To Bolster Data Security In The Cloud Siliconangle

Aws Cloudhsm Reviews Details Pricing Features G2

Choosing The Right Cloud Hsm Thales Blog
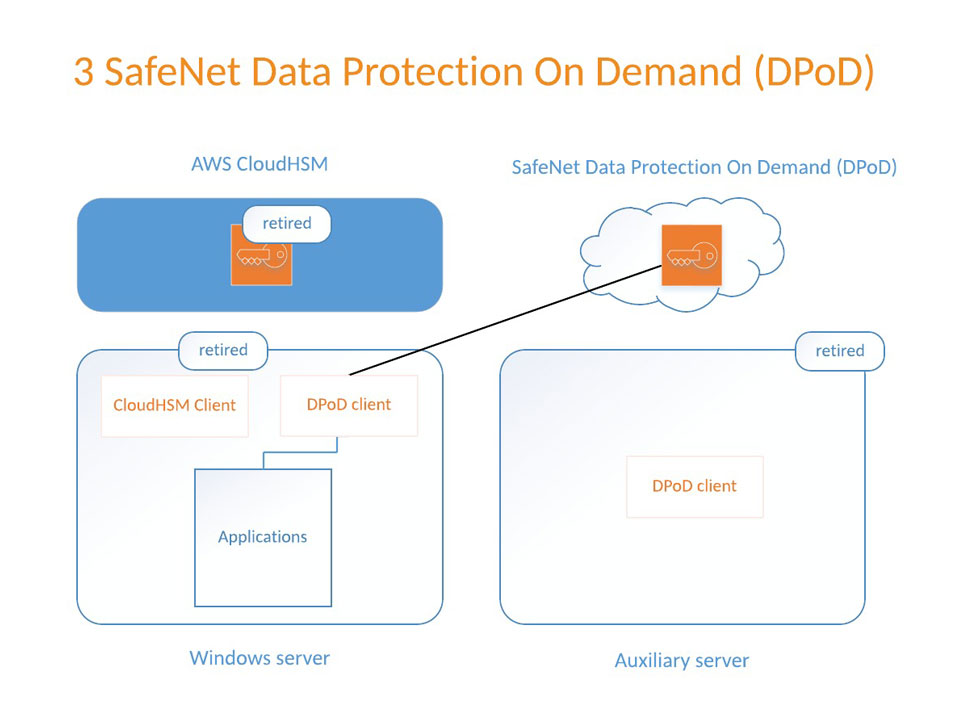
Take Control Of Your Cloudhsm Migration Plan Security Boulevard

Migrating From A Aws Cloudhsm Classic Partition
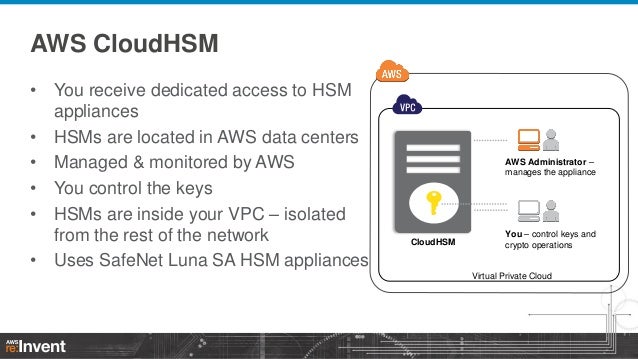
Encryption And Key Management In Aws Sec304 Aws Re Invent 13

What Is Aws Hsm Aws Cloudhsm Tutorial Links

How To Remove Single Points Of Failure By Using A High Availability Partition Group In Your Aws Cloudhsm Environment Aws Security Blog

Cloud Hsm Archives Cryptosense

Using Aws Cloudhsm To Protect Your Iis Private Key

Understanding Aws Cloudhsm Cluster Synchronization Aws Security Blog
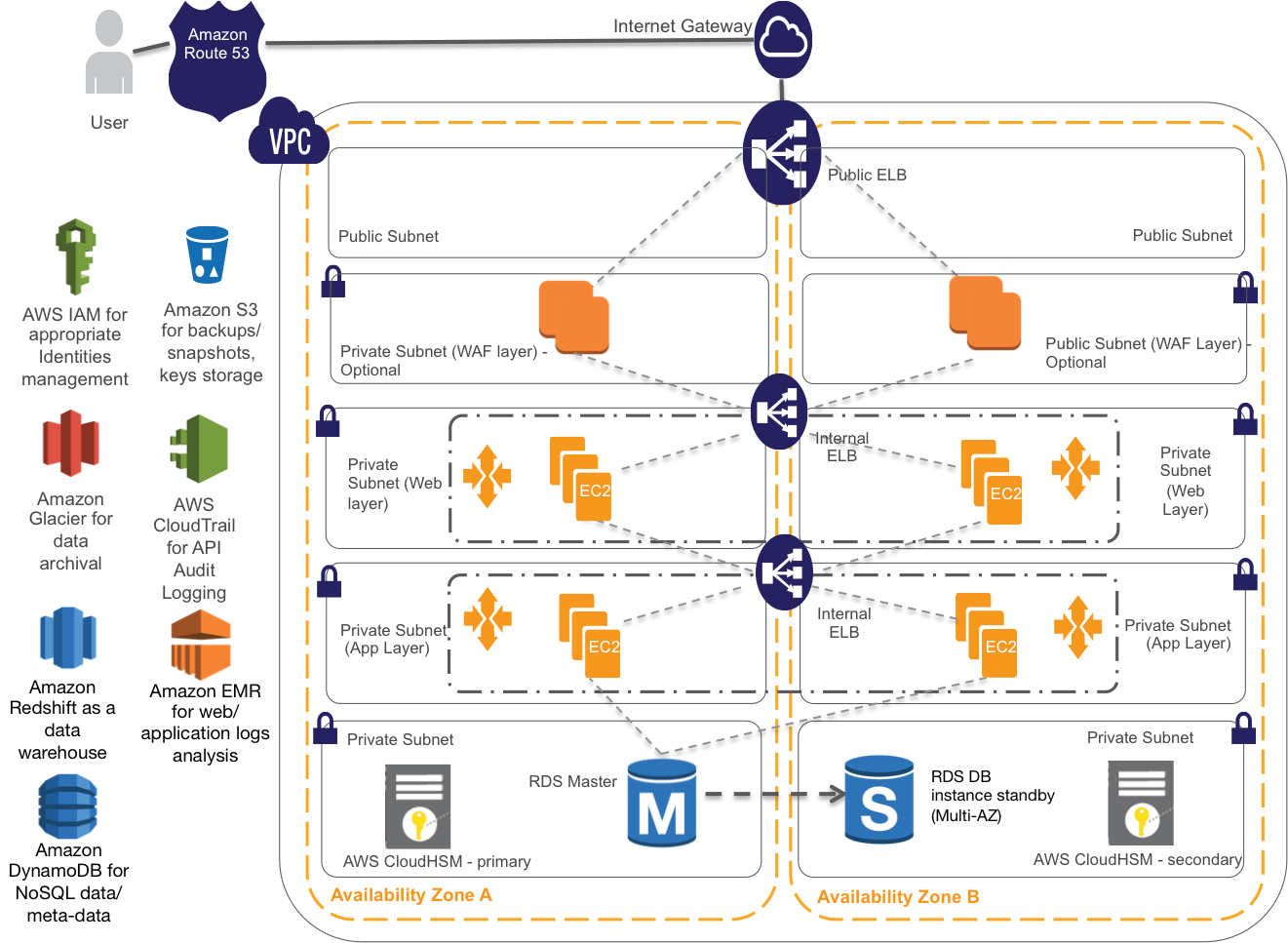
Architecting Your Healthcare Application For Hipaa Compliance Part 2 By Aws Startups Aws Startup Collection Medium

Aws Cloudhsm
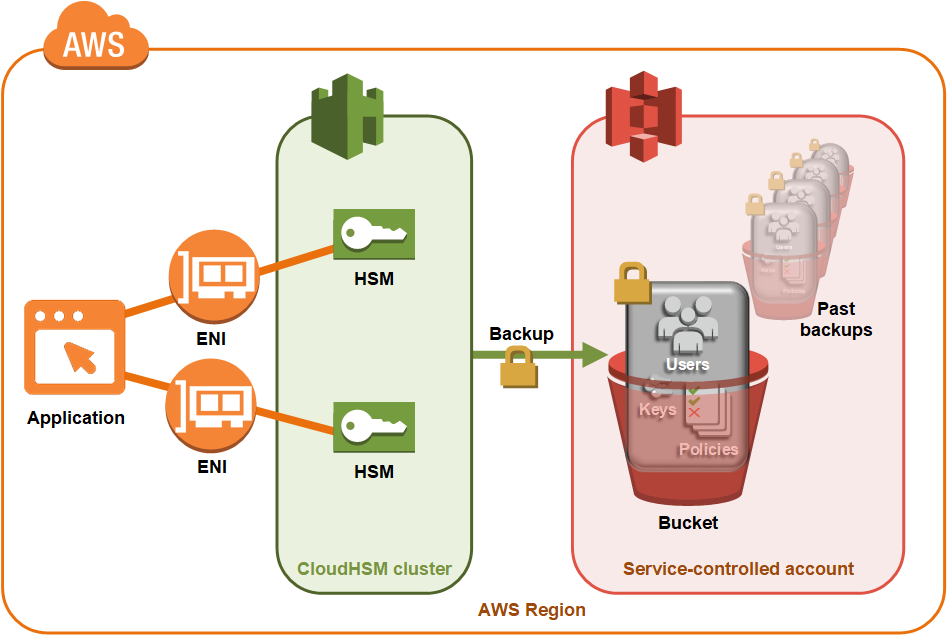
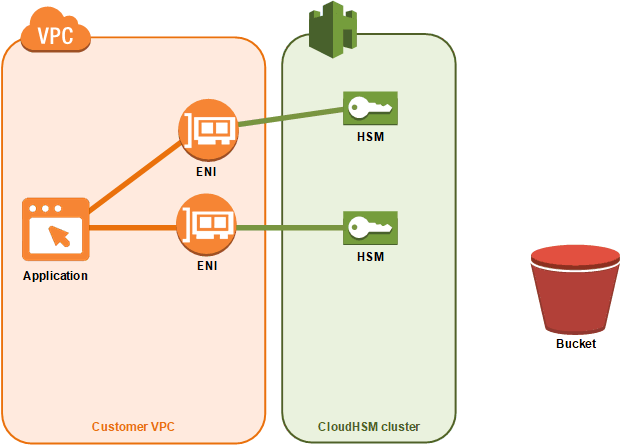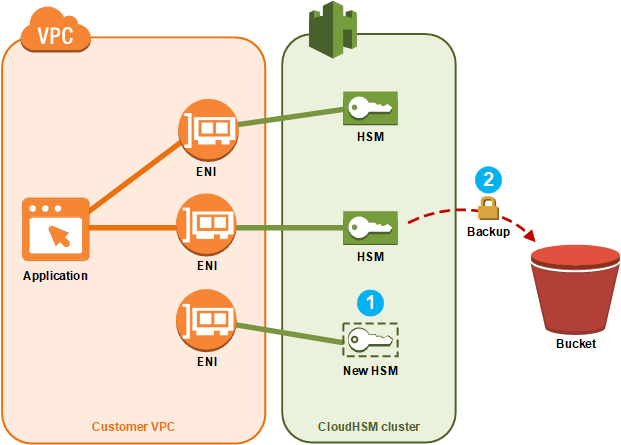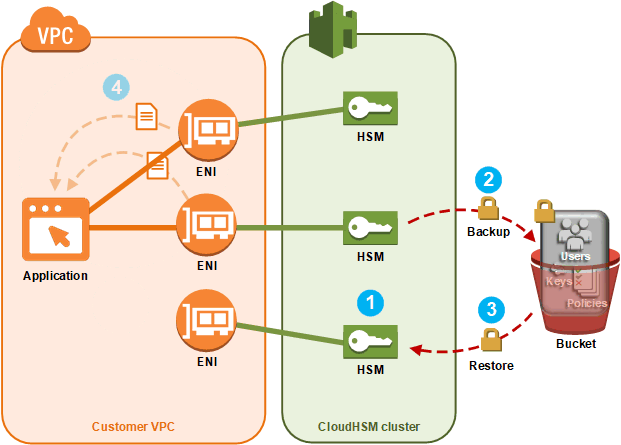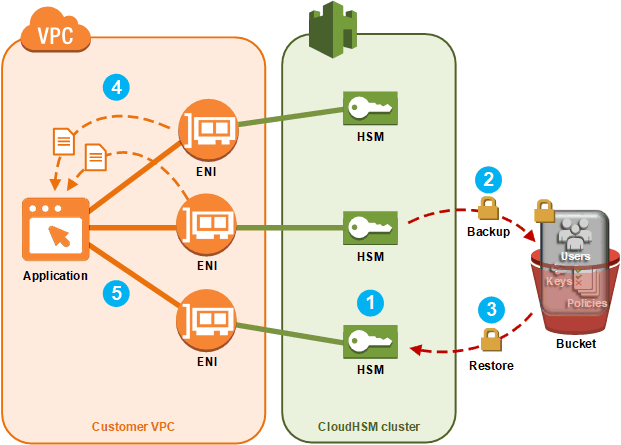
Aws Cloudhsm Cluster Backups Aws Cloudhsm
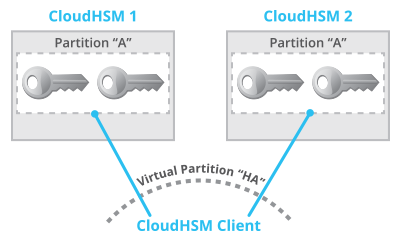
Aws Cloudhsm In High Availability Mode

Aws Black Belt Online Seminar Aws Cloudhsm Youtube

Aws Cloudhsm Another Amazing Service By Amazon Web Services Cloudreviews Cloud Hosting Cloud Storage Managed Hosting News Industry Updates Blog

Aws Advanced Technology Partner Modo
Q Tbn 3aand9gcrbbeaol96hfrlu0ac03nvke7yh9m Igy14d Lreqxnwhhsx Vg Usqp Cau
Cloudhsm Secure Scalable Key Storage In Aws 17 Aws Online Tech Talks Youtube
Aws Launches Cloudhsm App To Bolster Data Security In The Cloud Siliconangle

Aws Cloudhsm Digital Cloud Training

Aws Kms And Aws Cloudhsm Digital Cloud Training
D1 Awsstatic Com Whitepapers Security Security Of Aws Cloudhsm Backups Pdf

Aws Cloudhsm User Guide Aws Documentation Manualzz

Aws Cloudhsm The Modern Logic Group

Aws Architecture Diagrams Solution Aws Architecture Diagram Diagram Architecture Enterprise Application

Google Cloud Hsm Reviews Details Pricing Features G2
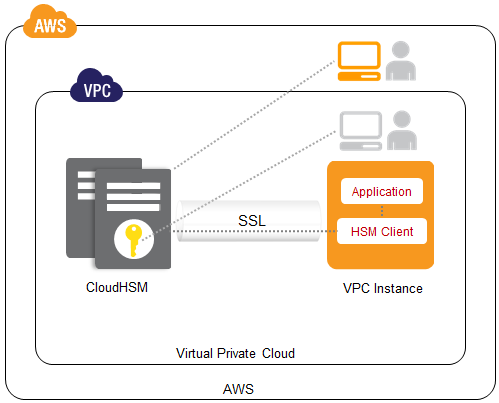
Aws Cloudhsm Secure Key Storage And Cryptographic Operations Aws News Blog

How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm Terabitweb Blog

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Aws Cloudhsm User Guide By Amazon Web Services

Aws Cloudhsm

How To Clone An Aws Cloudhsm Cluster Across Regions Aws Security Blog

Features Aws Cloudhsm Amazon Web Services Aws

How Secure Is Amazon S Key Management Service Aws Kms Interconnections The Equinix Blog
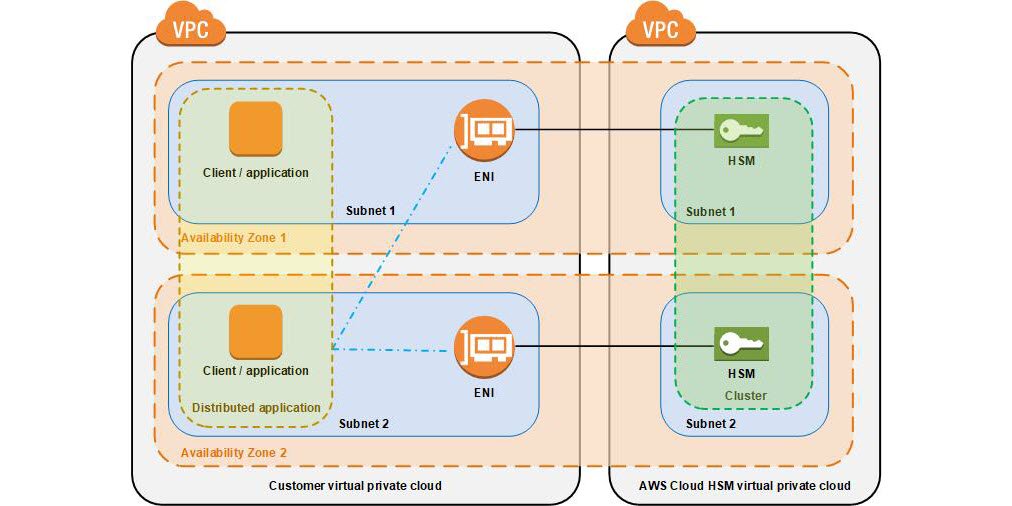
Amazon Web Services Aws Cloudhsm Now Provides Managed Hardware Security Modules In The Aws Cloud T Co Fpftcbna4i
Aws Cloudhsm Update Cost Effective Hardware Key Management At Cloud Scale For Sensitive Regulated Workloads M Square
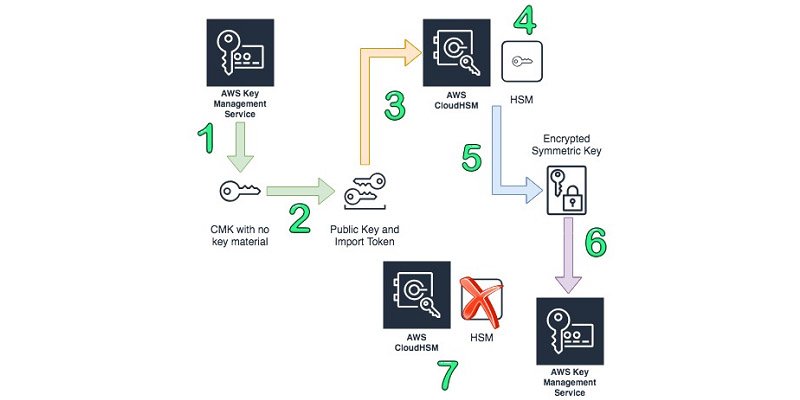
Aws Security Learn How To Byok Bring Your Own Key To Aws Kms For Less Than 15 00 A Year Using Aws Cloudhsm T Co 7sqet0fexu T Co Doxri2iani

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Terabitweb Blog

How To Run Aws Cloudhsm Workloads On Docker Containers Terabitweb Blog

Bloombase Storesafe Intelligent Storage Firewall Virtual Appliance Vmware Solution Exchange
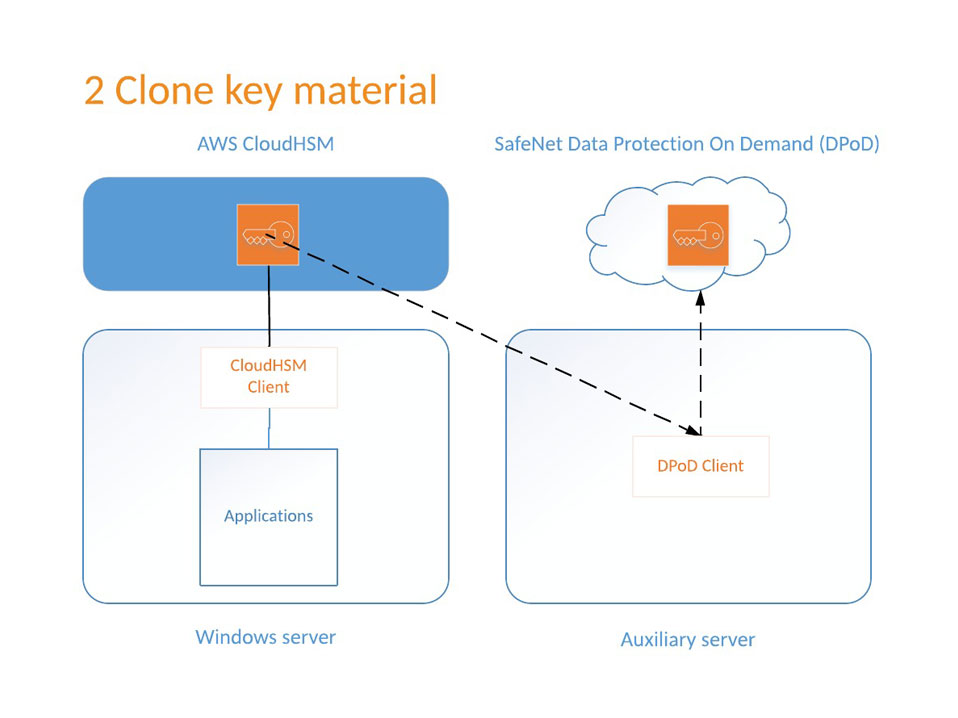
Take Control Of Your Cloudhsm Migration Plan Thales Blog
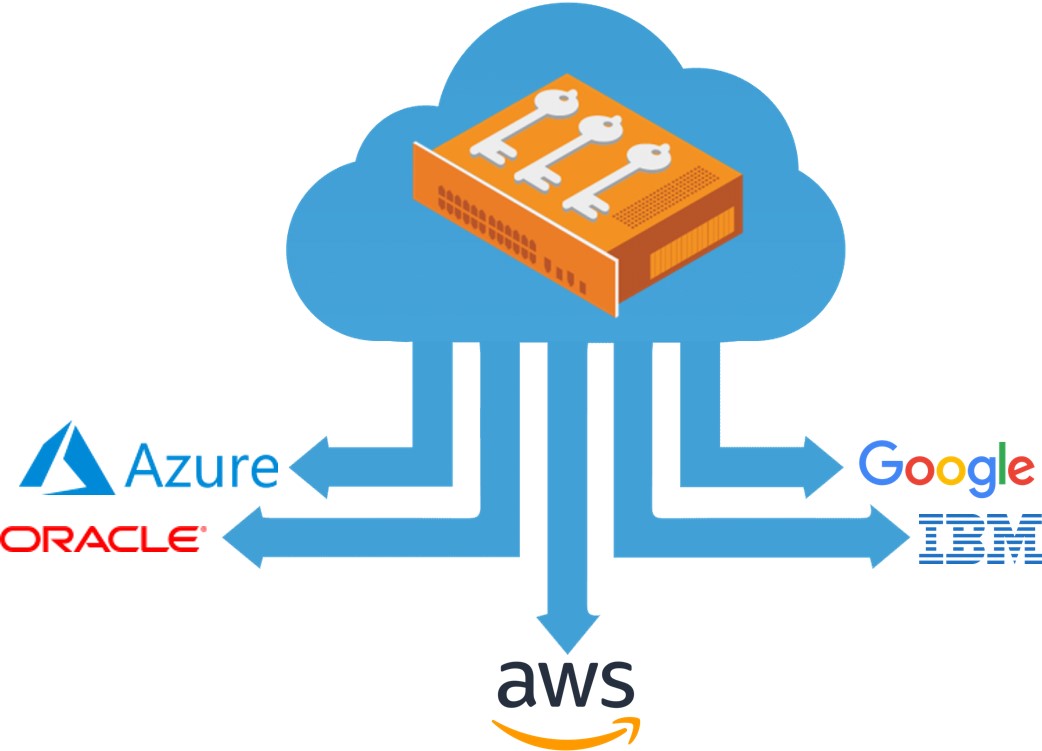
Choosing The Right Cloud Hsm Thales Blog
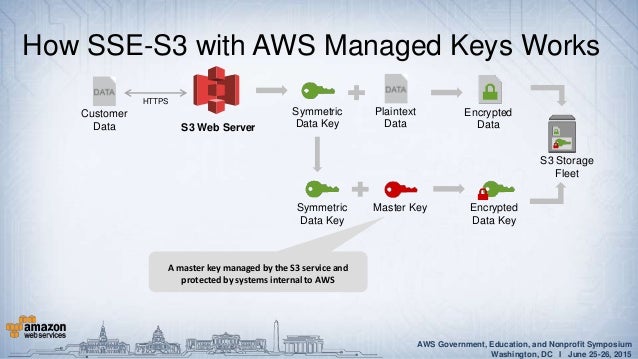
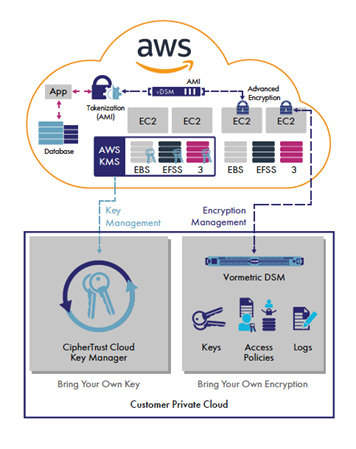
Protecting Your Data With Aws Kms And Aws Cloudhsm

Aws Cloudhsm Vs Vault What Are The Differences

How To Migrate A Digital Signing Workload To Aws Cloudhsm Terabitweb Blog

Cloudhsm Aws Security Blog

Use This New Aws Cloudhsm Tutorial To Amazon Web Services Facebook
D0 Awsstatic Com Whitepapers Aws Securing Data At Rest With Encryption Pdf
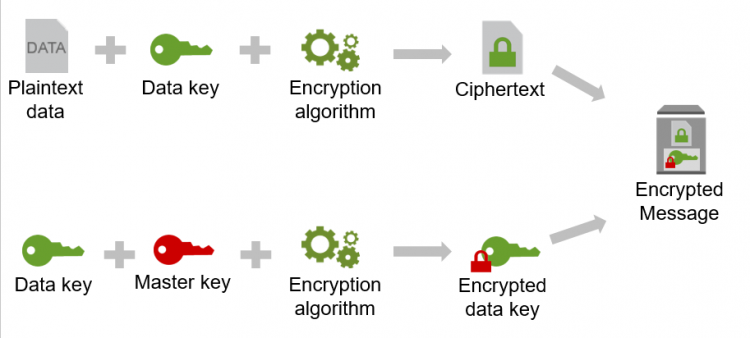
Determine Encryption Requirements Or Implementation Technologies Testprep Training Tutorials

Using Aws Cloudhsm Backed Certificates With Microsoft Internet Information Server Noise

How To Run Aws Cloudhsm Workloads On Aws Lambda Aws Security Blog

How To Migrate Symmetric Exportable Keys From Aws Cloudhsm Classic To Aws Cloudhsm Aws Security Blog

Aws Cloudhsm Aws Security Identity Compliance
Aws Cloudhsm V2 Dynatrace Help
Amazon Web Services Aws Cloud Computing Services
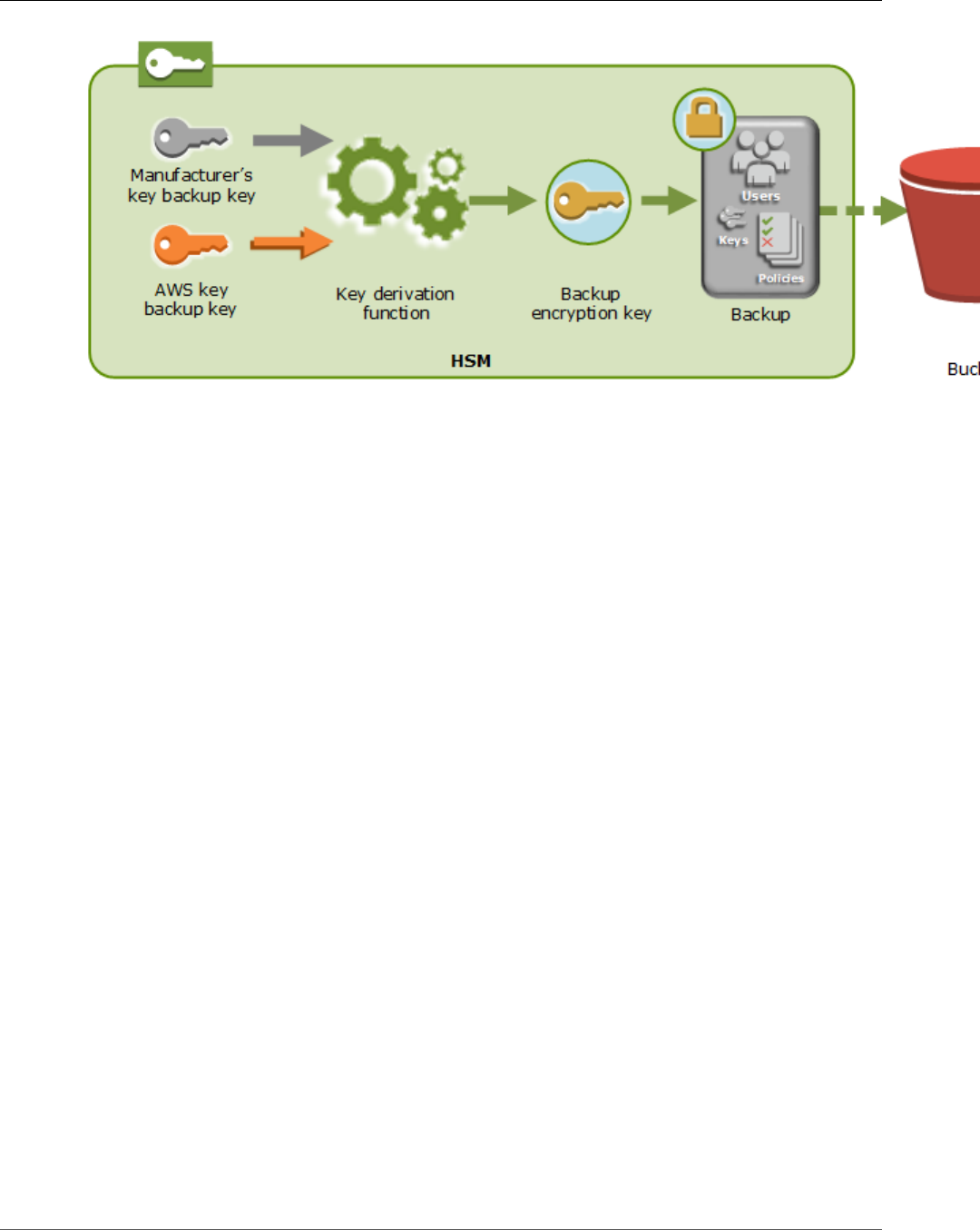
Aws Cloudhsm User Guide
Q Tbn 3aand9gcqz75 Ruyffvatuew8xvxj1czehlppub76pba Usqp Cau

Security Iteanz Com

Amazon Cloudhsm Aims To Ease Security Worries Informationweek

Deep Dive Aws Cloudhsm Classic

Aws Summit Series 17 New York Introducing The New Aws Cloudhsm Youtube

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings
Advanced Encryption Solutions For Amazon Web Services Thales

Aws Cloudhsm

How To Lower Costs By Automatically Deleting And Recreating Hsms Cyber Security And Consulting

Deep Dive Aws Cloudhsm Classic

Aws Cloudhsm Vs Google Cloud Endpoints What Are The Differences

Corda Enterprise 4 5 Aws Cloudhsm Support Corda
Q Tbn 3aand9gcrlxba7bkwaafa6cdftw1ulp1zjtohzin X Wvgxcexhov7eqm Usqp Cau
Protecting Your Data With Aws Kms And Aws Cloudhsm

Bring Your Own Key Byok Setup Process In Appian Cloud

Using Aws Kms Custom Key Store With Cloudhsm To Encrypt Your Data Cloud Architect Musings

Aws Cloudhsm
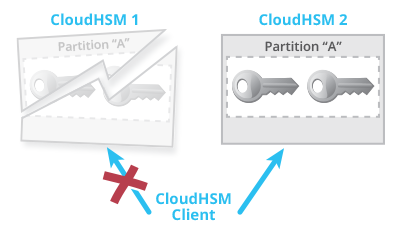
Aws Cloudhsm In High Availability Mode

Aws Cloudhsm Digital Cloud Training

Aws Kms And Aws Cloudhsm Digital Cloud Training

How To Deploy Cloudhsm To Securely Share Your Keys With Your Saas Provider Amazon Web Services Saas Deployment Network Layer

Aws Cloudhsm User Guide Hardcover Walmart Com Walmart Com

Aws Key Management Service Vs Aws Secrets Manager What Are The Differences
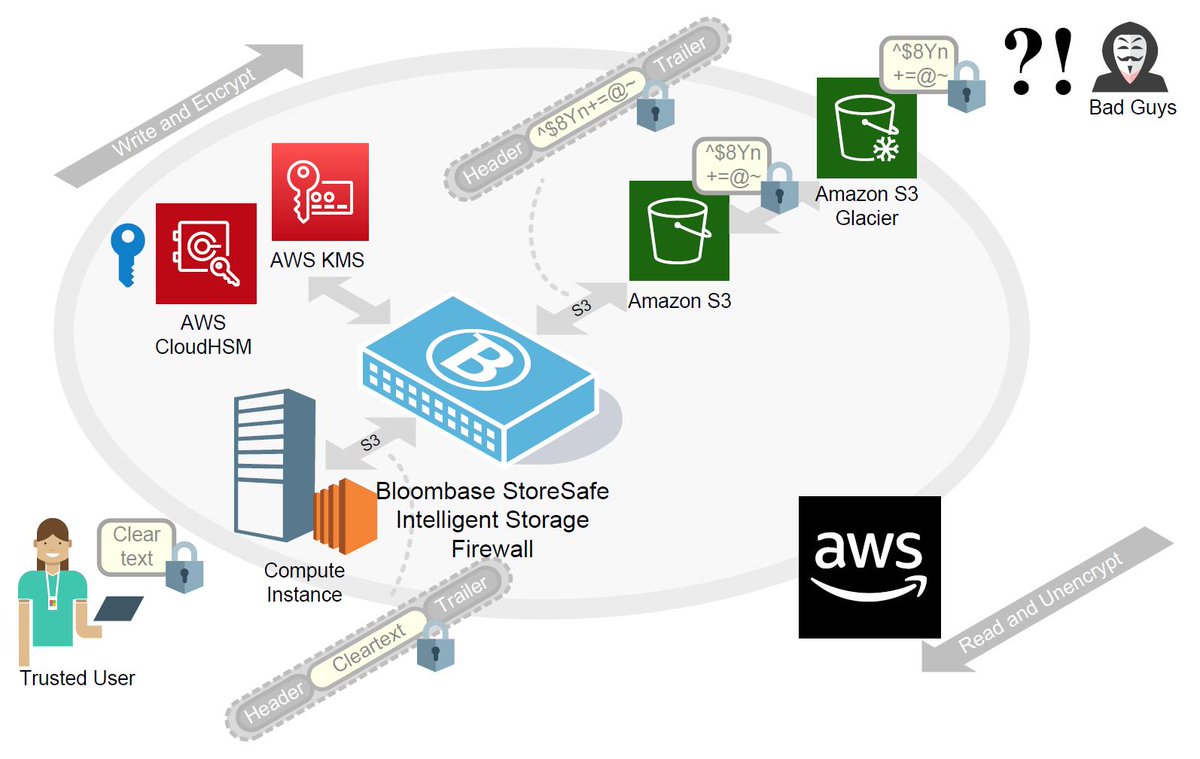
Avni Rambhia Avniramb Twitter
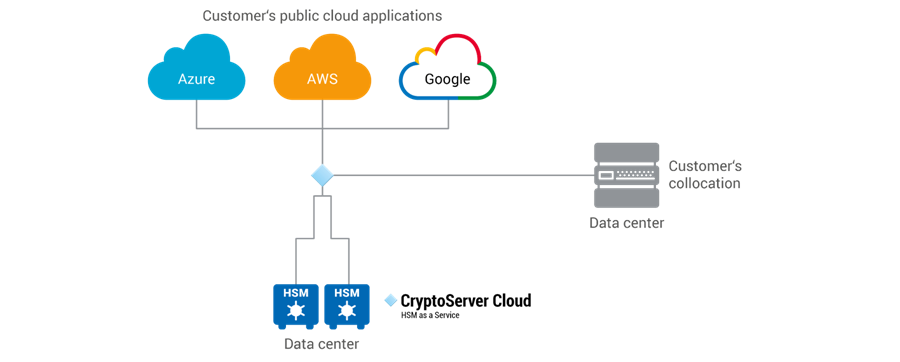
Hsm In The Cloud The Best Of Both Worlds For Cloud Security Encryption Consulting
Pages Awscloud Com Rs 112 Tzm 766 Images Protecting Sensitive Assets Aws Marketplace Sounil Yu Whitepaper Pdf

Aws Cloudhsm Dedicated Hardware Security Modu

Aws Cloudhsm Reviews Details Pricing Features G2

Deep Dive Aws Cloudhsm Classic

Aws Cloudhsm Adss Admin Guide

How To Update Aws Cloudhsm Devices And Client Instances To The Software And Firmware Versions Supported By Aws Aws Security Blog

Integration With Aws Cloudhsm Sso Connect Guide
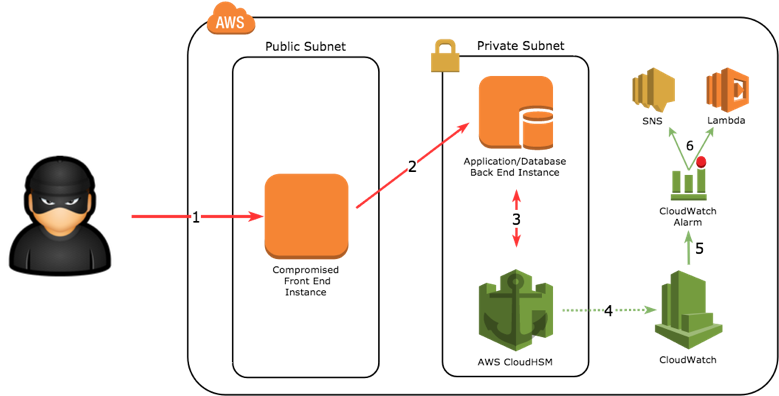
Crypto Anchoring Your Aws Environment Using Cloudhsm Credera

Bring Your Own Key Byok Setup Process In Appian Cloud

Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium

Aws Kms The Fully Managed Highly Available Aws By Crishantha Nanayakkara Medium

Aws Cloudhsm

Using Aws Cloudhsm In High Availability Mode
Q Tbn 3aand9gcrejirfjqubbxazmdeqo3z0prq3tjwvzfwo Nvp0ntb1sbxx7ln Usqp Cau



